- Managing Providers
- Infrastructure Providers
- Enabling Red Hat Virtualization Capacity and Utilization Data Collection
- Adding a Red Hat Virtualization Provider
- Authenticating Red Hat Virtualization Hosts
- Adding an OpenStack Infrastructure Provider
- Adding a VMware vCenter Provider
- Using a Non-Administrator Account for vCenter Hosts
- Authenticating VMware vCenter Hosts
- Authenticating to Microsoft SCVMM
- Adding a Microsoft SCVMM Provider
- Refreshing Providers
- Tagging Multiple Providers
- Viewing a Provider
- Removing a Provider
- Viewing the Provider Timeline
- Viewing Hosts and Clusters
- Viewing Virtual Machines and Templates
- Configuration Management Providers
- Adding an IBM Terraform Provider
- Triggering a Refresh of an IBM Terraform Provider
- Defining the Workflow
- Defining the Hostgroup Hierarchy
- Adding a Satellite 6 Provider
- Triggering a Refresh of a Satellite 6 Provider
- Displaying Red Hat Satellite 6 Contents
- Reprovisioning a Bare Metal Host
- Tagging a Bare Metal Host
- Automation Management Providers
- Credentials
- Tagging Ansible Playbooks, Repositories, and Credentials
- Optimizing Ansible Playbooks for ManageIQ
- Installing Roles on an Embedded Ansible Appliance
- Ansible Service Linking
- Callbacks in Multiple Appliance Environments
- Ansible Tower
- Working with an Ansible Tower Provider
- Adding an Ansible Tower Provider
- Refreshing an Ansible Tower Provider
- Viewing Ansible Tower Providers and Inventory
- Viewing Ansible Tower Configured Systems
- Executing an Ansible Tower Job or Workflow Template from a Service Catalog
- Executing an Ansible Tower Job Using a Custom Automate Button
- Ansible Tower
- Cloud Providers
- Adding OpenStack Providers
- Adding Azure Providers
- Adding Azure Cloud Regions
- Disabling Azure Cloud Regions
- Permissions for Amazon EC2 Providers
- Adding Amazon EC2 Providers
- Enabling Public AMIs from Amazon EC2
- Enabling AWS Config Notifications
- Enabling Amazon EC2 Events
- Adding Amazon Cloud Regions
- Disabling Amazon Cloud Regions
- Refreshing Cloud Providers
- Tagging Cloud Providers
- Removing Cloud Providers
- Editing a Cloud Provider
- Viewing a Cloud Provider’s Timeline
- IBM Cloud Virtual Server for VPC
- Adding IBM Cloud VPC Providers
- IBM Power Systems Virtual Servers
- Adding IBM Power Systems Virtual Servers Providers
- IBM PowerVC
- Adding IBM PowerVC Providers
- Network Managers
- Adding or Viewing Network Providers
- Refreshing Network Providers
- Tagging Network Providers
- Removing Network Providers
- Viewing a Network Provider’s Timeline
- Using the Topology Widget for Network Providers
- Containers Providers
- Adding an OpenShift Container Platform Provider
- Adding an Azure Kubernetes Service (AKS) Container Provider
- Adding an Oracle Kubernetes Engine (OKE) Container Provider
- Tagging Containers Providers
- Removing Containers Providers
- Editing a Containers Provider
- Hiding Environment Variables for Containers Providers
- Viewing a Containers Provider’s Timeline
- Storage Managers
- Viewing Object Stores
- Appendix
Managing Providers
ManageIQ can manage a variety of external environments, known as providers and managers. A provider or manager is any system that ManageIQ integrates with for the purpose of collecting data and performing operations.
In ManageIQ, a provider is an external virtualization, cloud, or containers environment that manages multiple virtual machines or instances residing on multiple hosts. One example is Red Hat Virtualization, a platform that manages multiple hosts and virtual machines.
In ManageIQ, a manager is an external management environment that manages more than one type of resource. One example of a manager is OpenStack, which manages infrastucture, cloud, network, and storage resources.
This guide covers working with providers and managers in ManageIQ, which include:
-
Infrastructure providers
-
Configuration management providers
-
Automation management providers
-
Cloud providers
-
Networking management providers
-
Middleware management providers
-
Container providers
-
Storage managers
For information on working with the resources contained by a provider or manager, see Managing Infrastructure and Inventory.
Infrastructure Providers
In ManageIQ, an infrastructure provider is a virtual infrastructure environment that you can add to a ManageIQ appliance to manage and interact with the resources in that environment. This chapter describes the different types of infrastructure providers that you can add to ManageIQ, and how to manage them. Infrastructure providers can be either discovered automatically by ManageIQ, or added individually.
The web interface uses virtual thumbnails to represent infrastructure providers. Each thumbnail contains four quadrants by default, which display basic information about each provider:

-
Number of hosts
-
Management system software
-
Currently unused
-
Authentication status
| Icon | Description |
|---|---|
 |
Validated: Valid authentication credentials have been added. |
 |
Invalid: Authentication credentials are invalid. |
 |
Unknown: Authentication status is unknown or no credentials have been entered. |
Provider authentication status
Red Hat Virtualization Providers
To use a Red Hat Virtualization provider, add it to the appliance and authenticate its hosts. You can also configure capacity and utilization data collection to help track usage and find common issues.
Enabling Red Hat Virtualization Capacity and Utilization Data Collection
Configure the following to collect capacity and utilization data from a Red Hat Virtualization provider:
-
In ManageIQ, enable the capacity and utilization server roles from the settings menu, in menu:Configuration[Server> Server Control]. For more information on capacity and utilization collection, see Assigning the Capacity and Utilization Server Roles in the Deployment Planning Guide.
-
For information on selecting clusters and datastores used to collect data, see Capacity and Utilization Data Collected in the General Configuration Guide.
-
In your Red Hat Virtualization environment, install the Data Warehouse and Reports components, and create a ManageIQ user in the Data Warehouse database:
-
To install the Data Warehouse and Reports components in a Red Hat Virtualization environment, see the Data Warehouse Guide.
-
To create a ManageIQ user in the Data Warehouse database, see Data Collection for Red Hat Enterprise Virtualization in the Deployment Planning Guide.
-
Adding a Red Hat Virtualization Provider
After initial installation and creation of a ManageIQ environment, add a Red Hat Virtualization provider to the appliance.
-
Browse to menu: Compute > Infrastructure > Providers.
-
Click Configuration, then click
 Add a New Infrastructure Provider.
Add a New Infrastructure Provider. -
Select Red Hat Virtualization from the Type list.
-
Enter a Name for the provider.
-
Select the appropriate Zone for the provider. If you do not specify a zone, it is set to default.
-
Under Endpoints in the Default tab, configure the following:
-
Enter the Hostname or IPv4 or IPv6 address of the Red Hat Virtualization Manager.
Important:
The Hostname must be a unique fully qualified domain name.
-
Select Verify or Do not verify for SSL Verification to specify whether to authenticate securely to the provider using SSL.
- If you select Verify for SSL Verification, you can either paste a custom certificate in the Trusted CA Certificates field in PEM format, or leave the Trusted CA Certificates field empty if your Red Hat Virtualization provider has a trusted Certificate Authority.
-
Enter the API Port if your provider uses a non-standard port for access.
-
Provide the login credentials for the Red Hat Virtualization administrative user:
-
Enter the user name (formatted as
admin@internal) in the Username field. -
Enter the password in the Password field.
-
Click Validate to confirm ManageIQ can connect to the Red Hat Virtualization Manager.
-
-
-
Under Endpoints in the Metrics tab, you can configure capacity and utilization metrics collection by providing login credentials for the ManageIQ user of the Red Hat Virtualization Data Warehouse database. You can also configure this later by editing the provider. Configure the following in the Metrics tab:
Important
To collect capacity and utilization data from a Red Hat Virtualization provider, the capacity and utilization server roles must be enabled in ManageIQ. The Red Hat Virtualization environment must also contain the Data Warehouse and Reports components and a ManageIQ user. Specific clusters, hosts, and datastores can also be configured for collection. See Enabling Red Hat Virtualization Capacity and Utilization Data Collection for configuration details.
-
Enter the database hostname or IPv4 or IPv6 address in Hostname.
-
Enter the API Port if your provider uses a non-standard port for access.
-
Enter the database user name in the Username field.
-
Enter the user password in the Password field.
-
Enter the Database Name.
-
Click Validate to confirm ManageIQ can connect to the database.
-
-
Click Add to finish adding the Red Hat Virtualization provider.
Authenticating Red Hat Virtualization Hosts
After adding a Red Hat Virtualization infrastructure provider, you must authenticate its hosts to enable full functionality.
-
Browse to menu: Compute > Infrastructure > Providers.
-
Click on a provider to display its summary screen.
-
On the summary screen, click Hosts in the Relationships information box to display the hosts on that provider.
-
Select the hosts to authenticate. You can select all hosts using the Check All option.
-
Click Configuration.
-
Click
 (Edit this item).
(Edit this item). -
In the Credentials area, enter credentials for the following, as required:
-
Default: This field is mandatory. Users should have privileged access such as, root or administrator.
-
Remote Login: Credentials for this field are required if SSH login is disabled for the Default account.
-
Web Services: This tab is used for access to Web Services in Red Hat Virtualization.
-
IPMI: This tab is used for access to IPMI.
-
-
Click Validate.
-
If editing multiple hosts:
-
Select a host from the Select Host to validate against list.
-
If required, enter credentials for Remote Login, Web Services, and IPMI in their respective tabs; click Validate.
-
Select another host to validate each of these credentials against.
-
-
Click Add.
OpenStack Infrastructure Providers
Enable an OpenStack Infrastructure provider by adding it to the appliance.
Adding an OpenStack Infrastructure Provider
After initial installation and creation of a ManageIQ
environment, add an OpenStack infrastructure provider to the appliance.
ManageIQ supports operating with the OpenStack admin tenant.
When creating an OpenStack infrastructure provider in ManageIQ,
select the OpenStack infrastructure provider’s admin user because it
is the default administrator of the OpenStack admin tenant. When using
the admin credentials, a user in ManageIQ provisions into the
admin tenant, and sees images, networks, and instances that are
associated with the admin tenant.
Note:
-
You can set whether ManageIQ should use the Telemetry service or Advanced Message Queueing Protocol (AMQP) for event monitoring. If you choose Telemetry, you should first configure the ceilometer service on the undercloud to store events. See Configuring the Undercloud to Store Events for instructions. For more information, see OpenStack Telemetry (ceilometer) in the Red Hat OpenStack Platform Architecture Guide.
-
To authenticate the provider using a self-signed Certificate Authority (CA), configure the ManageIQ appliance to trust the certificate using the steps in Using a Self-Signed CA Certificate before adding the provider.
-
Browse to menu: Compute > Infrastructure > Providers.
-
Click Configuration, then click
 (Add
a New Infrastructure Provider).
(Add
a New Infrastructure Provider). -
Enter the Name of the provider to add. The Name is how the device is labeled in the console.
-
Select OpenStack Platform Director from the Type list.
-
Select the API Version of your OpenStack provider’s Keystone service from the list. The default is
Keystone v2.Note:
- With Keystone API v3, domains are used to determine administrative boundaries of service entities in OpenStack. Domains allow you to group users together for various purposes, such as setting domain-specific configuration or security options. For more information, see OpenStack Identity (keystone) in the Red Hat OpenStack Platform Architecture Guide.
- The provider you are creating will be able to see projects for the given domain only. To see projects for other domains, add it as another cloud provider. For more information on domain management in OpenStack, see Domain Management in the Red Hat OpenStack Platform Users and Identity Management Guide.
-
Select the appropriate Zone for the provider. By default, the zone is set to default.
Note:
For more information, see the definition of host aggregates and availability zones in OpenStack Compute (nova) in the Red Hat OpenStack Platform Architecture Guide.
-
In the Default tab, under Endpoints, configure the host and authentication details of your OpenStack provider:
-
Select a Security Protocol method to specify how to authenticate the provider:
-
SSL without validation: Authenticate the provider insecurely using SSL.
-
SSL: Authenticate the provider securely using a trusted Certificate Authority. Select this option if the provider has a valid SSL certificate and it is signed by a trusted Certificate Authority. No further configuration is required for this option. This is the recommended authentication method.
-
Non-SSL: Connect to the provider insecurely using only HTTP protocol, without SSL.
-
-
Enter the Host Name or IP address(IPv4 or IPv6) of the provider. If your provider is an undercloud, use its hostname (see Setting the Hostname for the System in Red Hat OpenStack Platform Director Installation and Usage for more details)
-
In API Port, set the public port used by the OpenStack Keystone service. By default, OpenStack uses port 5000 for non-SSL security protocol. For SSL, API port is 13000 by default.
-
In the Username field, enter the name of an OpenStack user with privileged access (for example, admin). Then, provide its corresponding password in the Password and Confirm Password fields.
-
Click Validate to confirm ManageIQ can connect to the OpenStack provider.
-
-
Next, configure how ManageIQ should receive events from the OpenStack provider. Click the Events tab in the Endpoints section to start.
-
To use the Telemetry service of the OpenStack provider, select Ceilometer. Before you do so, the provider must first be configured accordingly. See Configuring the Undercloud to Store Events for details.
-
If you prefer to use the AMQP Messaging bus instead, select AMQP. When you do: In Hostname (or IPv4 or IPv6 address) (of the Events tab, under Endpoints), enter the public IP or fully qualified domain name of the AMQP host.
-
In the API Port, set the public port used by AMQP. By default, OpenStack uses port 5672 for this.
-
In the Username field, enter the name of an OpenStack user with privileged access (for example, admin). Then, provide its corresponding password in the Password field.
-
Click Validate to confirm the credentials.
-
-
-
You can also configure SSH access to all hosts managed by the OpenStack infrastructure provider. To do so, click on the RSA key pair tab in the Endpoints section.
-
From there, enter the Username of an account with privileged access.
-
If you selected SSL in Endpoints > Default > Security Protocol earlier, use the Browse button to find and set a private key.
-
-
Click Add after configuring the infrastructure provider.
Note:
ManageIQ requires that the adminURL endpoint for all OpenStack services be on a non-private network. Accordingly, assign the adminURL endpoint an IP address of something other than 192.168.x.x. The adminURL endpoint must be accessible to the ManageIQ appliance that is responsible for collecting inventory and gathering metrics from the OpenStack environment. Additionally, all the Keystone endpoints must be accessible, otherwise refresh will fail.
Configuring the Undercloud to Store Events
To allow ManageIQ to receive events from a Red Hat OpenStack Platform environment, you must configure the notification_driver option for the Compute service and Orchestration service in that environment. See Installing the Undercloud and Configuring the Director in Red Hat OpenStack Platform Director Installation and Usage for related details.
VMware vCenter Providers
To use a VMware vCenter provider, add it to the appliance and authenticate its hosts.
Adding a VMware vCenter Provider
After initial installation and creation of a ManageIQ environment, add a VMware vCenter provider to the appliance.
-
Browse to menu: Compute > Infrastructure > Providers.
-
Click Configuration, then click
 (Add
a New Infrastructure Provider).
(Add
a New Infrastructure Provider). -
Enter the Name of the provider to add. The Name is how the device is labeled in the console.
-
Select VMware vCenter from the Type list.
-
Enter the Host Name or IP address(IPv4 or IPv6) of the provider.
The **Host Name** must use a unique fully qualified domain name. -
Select the appropriate Zone for the provider. By default, the zone is set to default.
-
Optional: Enter the Host Default VNC Start Port and Host Default VNC End Port. These properties are used for remote console access with VNC. If VNC is available from the hosts, list the available port range using the start and end port.
-
In the Credentials area, under Default, provide the login credentials required for the VMware vCenter administrative user:
-
Enter the user name in the Username field.
-
Enter the password in the Password field.
-
Confirm the password in the Confirm Password field.
-
Click Validate to confirm ManageIQ can connect to the VMware vCenter.
-
-
Click Add.
Using a Non-Administrator Account for vCenter Hosts
After adding a VMware vCenter infrastructure provider, you must authenticate its hosts to enable full functionality. You can use administrator credentials, or create another user assigned to a role created for ManageIQ. See the VMware documentation for instructions on how to create a role.
The following privileges should be enabled for the non-administrator user:
From the Global group, check:
-
Cancel task
-
Diagnostics
-
Log Event
-
Set custom attribute
-
Settings
Check the entire set of privileges for the following groups:
-
Alarms
-
Datastores
-
dvPort Group
-
Host
-
Network
-
Resource
-
Scheduled Task
-
Tasks
-
Virtual Machine
-
vSphere Distributed Switch
Additionally, you must assign the new role to the following objects:
-
Datacenter: At the Datacenter the ManageIQ user/group must have at least the read-only role at the Datacenter level (Not Propagated) to be able to see the datacenter. Without this access, relationships cannot be made. Specifically, the datastores will not show up.
-
Cluster: Each Cluster that the ManageIQ needs access to must have the new role assigned and propagated.
-
Folders: Each Folder that ManageIQ needs access to must have the new role assigned and propagated.
-
Datastores: Each Datastore that ManageIQ needs access to must have the new role assigned and propagated.
-
Networking: Each vLAN or Port Group that ManageIQ needs access to must have the new role assigned and propagated.
Authenticating VMware vCenter Hosts
The procedure below describes how to authenticate the VMware vCenter hosts.
-
Browse to menu: Compute > Infrastructure > Providers.
-
Click on a provider to display its summary screen.
-
On the summary screen, click Hosts in the Relationships information box to display the hosts on that provider.
-
Select the hosts to authenticate. You can select all hosts using the Check All option.
-
Click Configuration
-
Click
 (Edit Selected
items).
(Edit Selected
items). -
In the Credentials area, under Default, provide the VMware ESXi login credentials:
-
Enter the user name in the Username field.
-
Enter the password in the Password field.
-
Confirm the password in the Confirm Password field.
-
Click Validate to confirm ManageIQ can connect to the VMware vCenter host.
-
-
If editing multiple hosts, select a host from the Select Host to validate against list; provide the VMware ESXi login credentials and click Validate.
-
Click Save.
Microsoft SCVMM Providers
To use a Microsoft System Center Virtual Machine Manager (SCVMM) provider, add it to the appliance and set up the SCVMM server for authentication.
Note:
To use a SCVMM provider, you must have at least one network adapter available for communication between the host and the SCVMM management server. Make sure that Used by Management is checked for this network adapter in the SCVMM host properties.
Authenticating to Microsoft SCVMM
Before you can add a Microsoft SCVMM provider to your ManageIQ environment, you must enable WinRM to listen for HTTP traffic on Microsoft SCVMM servers. You must also set the appropriate execution policy on the Microsoft SCVMM server to allow PowerShell scripts from the appliance to run remotely.
-
Log in to the Microsoft SCVMM server.
-
Enable WinRM for configuration.
winrm quickconfig -
Set the following options:
winrm set winrm/config/client/auth @{Basic="true"} winrm set winrm/config/service/auth @{Basic="true"} winrm set winrm/config/service @{AllowUnencrypted="true"} -
For Windows 2012 R2 with PowerShell 4.0, use the following syntax to set these options:
winrm set winrm/config/client/auth '@{Basic="true"}' winrm set winrm/config/service/auth '@{Basic="true"}' winrm set winrm/config/service '@{AllowUnencrypted="true"}' -
Enable remote script execution on the SCVMM server using the Set-ExecutionPolicy cmdlet.
Set-ExecutionPolicy RemoteSignedFor more information on SCVMM remote script execution policies, see Using the Set-ExecutionPolicy Cmdlet.
If PowerShell returns an error, search for log_dos_error_results in
the evm.log and scvmm.log files for information.
Adding a Microsoft SCVMM Provider
After initial installation and creation of a ManageIQ environment, add a Microsoft System Center Virtual Machine Manager (SCVMM) provider to the appliance.
Note:
To authenticate the provider using a self-signed Certificate Authority (CA), configure the ManageIQ appliance to trust the certificate using the steps in Using a Self-Signed CA Certificate before adding the provider.
-
Browse to menu: Compute > Infrastructure > Providers.
-
Click Configuration, then click
 (Add a New Infrastructure Provider).
(Add a New Infrastructure Provider). -
Enter the Name of the provider to add. The Name is how the device is labeled in the console.
-
Select Microsoft System Center VMM from the Type list.
-
Enter the Host Name or IP address(IPv4 or IPv6) of the provider.
The **Host Name** must use a unique fully qualified domain name. -
Select Kerberos or Basic (SSL) from the Security Protocol list.
-
For Kerberos:
-
Enter the user name and realm in the Username field.
-
Enter the password in the Password field.
-
Enter the password again in the Confirm Password field.
-
-
For Basic (SSL):
-
Enter the user name in the Username field.
-
Enter the password in the Password field.
-
Enter the password again in the Confirm Password field.
-
-
-
Click Validate to confirm that ManageIQ can connect to the Microsoft System Center Virtual Machine Manager.
-
Click Add.
Refreshing Providers
Refresh a provider to find other resources related to it. Use
Refresh after initial discovery to get the latest data about the
provider and the virtual machines it can access. Ensure the provider has
credentials to do this. If the providers were added using Discovery,
add credentials using  (Edit Selected Infrastructure Provider).
(Edit Selected Infrastructure Provider).
-
Browse to menu: Compute > Infrastructure > Providers.
-
Select the providers to refresh.
-
Click Configuration, and then
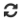 (Refresh Relationships and Power States).
(Refresh Relationships and Power States). -
Click OK.
Tagging Multiple Providers
Apply tags to all providers to categorize them together at the same time.
-
Navigate to menu:Infrastructure[Providers].
-
Check the providers to tag.
-
Click
 (Policy), and then
(Policy), and then  (Edit Tags).
(Edit Tags). -
In the Tag Assignment area, select a customer tag to assign from the first list, then select a value to assign from the second list.
-
Select more tags as required; click (Save).
Viewing a Provider
From a list of providers, you can review a specific provider by clicking on it. This displays various options to access provider information.
There are two methods of viewing an infrastructure provider’s details:
the summary screen (default) and the dashboard screen. Use the summary
 and dashboard
and dashboard
 buttons to toggle between views.
buttons to toggle between views.
Both the summary and dashboard screens contain a taskbar with Reload, Configuration, Policy, Monitoring, and Authentication buttons to manage the selected provider.
Provider Summary Screen.
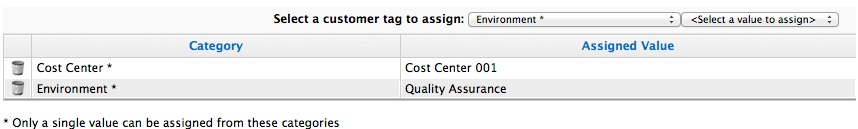
The provider summary screen displays information about the provider in table format.
-
Provider accordion: Displays details about the provider’s Properties and Relationships on the sidebar. Click to expand these lists.
-
Provider summary: Displays a provider’s Properties, Status, Relationships, and Smart Management. Click on an item in the Relationships table to see more information about that entity.
Provider Dashboard Screen.
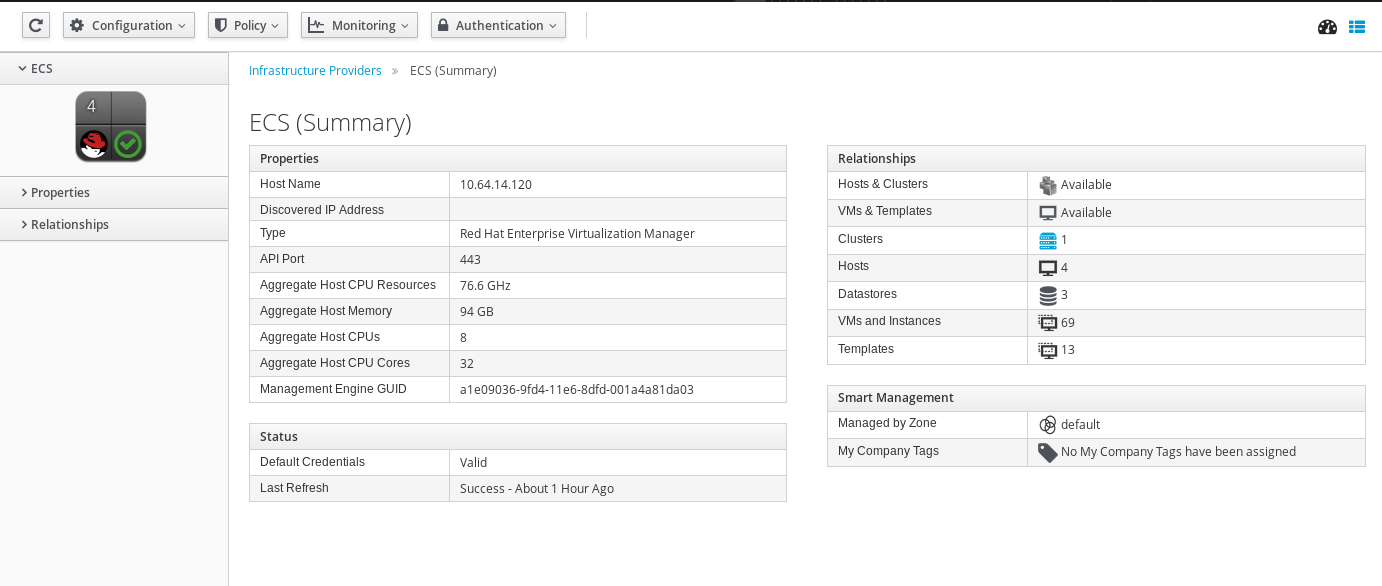
From the dashboard, you can view:
-
Number of clusters, hosts, virtual machines, templates, datastores, resource pools, and other entities on the provider. Click on an entity to see more information about that item.
-
Aggregate utilization for CPU, memory, and storage
-
Network I/O statistics
-
Trends for hosts and virtual machines discovered
To view the dashboard:
-
Browse to menu: Compute > Infrastructure > Providers.
-
Click the infrastructure provider to view.
-
To access the dashboard view, click
 (Dashboard view).
(Dashboard view).
To return to the summary view, click  (Summary view).
(Summary view).
Removing a Provider
If a provider has been decommissioned or requires some troubleshooting, it might require deletion from the VMDB.
Deleting a provider removes the account information from ManageIQ console. You will no longer be able to view any associated history including chargeback reports generated for the deleted provider. Additionally, if ManageIQ is the database of record, deleting providers would become a major problem for the other systems relying on it for accurate and consistent billing information. Review all the dependencies carefully before deleting a provider.
-
Navigate to menu:Compute[Infrastructure > Providers].
-
Select the check box for the provider to delete.
-
Click
 (Configuration), then
(Configuration), then
 (Remove Infrastructure Providers from the VMDB).
(Remove Infrastructure Providers from the VMDB). -
Click (OK).
Viewing the Provider Timeline
View the timeline of events for the virtual machines registered to a provider.
-
Navigate to menu:Compute[Infrastructure > Providers].
-
Click a provider.
-
Click
 (Monitoring), and then
(Monitoring), and then
 (Timelines)from the taskbar, or
from the provider accordion, click menu:Properties[Timeline].
(Timelines)from the taskbar, or
from the provider accordion, click menu:Properties[Timeline]. -
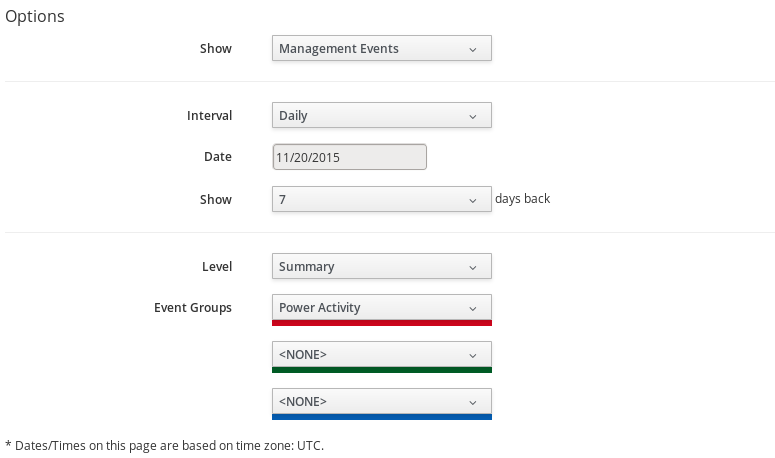
From Options, customize the period of time to display and the types of events to see.
-
Use Show to select regular Management Events or Policy Events.
-
Use the Interval dropdown to select hourly or daily data points.
-
Use Date to type the date for the timeline to display.
-
If you select to view a daily timeline, use Show to set how many days back to go. The maximum history is 31 days.
-
The three Event Groups lists allow you to select different groups of events to display. Each has its own color.
-
From the Level list, select a Summary event, or a Detail list of events. For example, the detail level of a Power On event might include the power on request, the starting event, and the actual Power On event. If you select Summary, only the Power On event displays in the timeline.
-
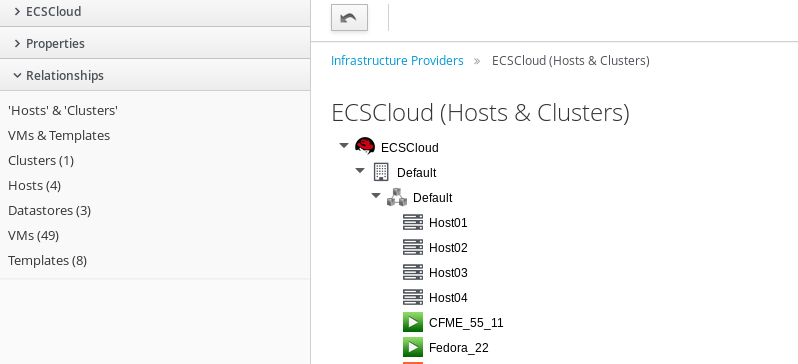
Viewing Hosts and Clusters
Access a tree view of the hosts and clusters for a provider from the Provider Summary.
-
Navigate to menu:Compute[Infrastructure > Providers].
-
Click the provider to view the hosts and clusters.
-
Click on the Relationships accordion, then click Hosts & Clusters.
Viewing Virtual Machines and Templates
Access a tree view of the virtual machines and templates for a provider from the Provider Summary.
-
Navigate to menu:Compute[Infrastructure > Providers].
-
Click the provider to view the virtual machines and templates.
-
From accordion menu, click Relationships, then click VMs & Templates.
Configuration Management Providers
In ManageIQ, a configuration management provider is a systems management product that you can add to a ManageIQ appliance to manage the lifecycle of your resources. Configuration management providers are useful for uniformly applying changes and updates across providers, and for recording and reporting status and change activity. They can also help eliminate the confusion and error brought about by the existence of different providers.
This chapter describes the different types of configuration management providers available to ManageIQ, and how to manage them. Configuration management providers must be added individually to ManageIQ.
IBM Terraform provider
ManageIQ includes an IBM Terraform provider that provides functionality to integrate with the Managed Services component. Managed services uses open source Terraform to manage and deliver cloud infrastructure as code. Terraform is an Open Source software that is developed by HashiCorp that enables predictable and consistent provisioning of many cloud platforms, classic infrastructure, and virtual private cloud (VPC) infrastructure resources by using a high-level scripting language. You can use Terraform to automate your cloud resource provisioning, rapidly build complex, multi-tier cloud environments, and enable Infrastructure as Code (IaC). ManageIQ provides functionality to integrate with Terraform and take advantage of features. This includes:
-
Discovering the inventory from Managed Services, including templates, stacks, and virtual machines provisioned using Terraform.
-
Providing traceability between VM resources provisioned by Terraform and discovered by ManageIQ.
-
Applying ManageIQ policy tags to hosts.
Adding an IBM Terraform Provider
To start discovering the Terraform templates and virtual machines, you need at least one IBM Terraform provider added to ManageIQ.
-
Browse to menu: Configuration > Providers.
-
Select menu: Configuration > Add a new Provider.
-
Select Type as IBM Terraform Configuration
-
Enter a Name for the provider.
- Select a Zone, choose default.
In the Endpoint section:
-
Enter the Managed Services URL for the provider.
This is the URL for Managed Services and can be either an IP address or a hostname.
For example,
https://cam.apps.test.example.com. -
In the
Endpointsection, enter the CloudPak for MCM URL. This is the console URL for the IBM CloudPak for Multicloud Management system. This is used for authentication and access token.For example,
https://cp-console.apps.test.example.com. -
Select SSL verification as Verify or Do not verify.
-
Enter a Username for a user on the provider. This must be a user in IBM CloudPak for Multicloud Management.
-
Enter a Password.
-
Click Validate to test your connection.
- Click Add to confirm your settings and save the provider.
ManageIQ saves the IBM Terraform provider in its database and triggers a refresh of resources detected in the provider.
Triggering a Refresh of an IBM Terraform Provider
Your IBM Terraform provider can still create new hosts independently of ManageIQ. Your ManageIQ detects these changes after an automatic refresh period. However, you can trigger a manual refresh to avoid waiting for the automatic refresh.
-
Navigate to menu: Configuration > Providers.
-
Select your Terraform provider using the checkbox, and click menu: Configuration > Refresh Relationships and Power States. This triggers the refresh.
-
When the refresh is complete, select the Terraform provider to check the updated list of Configuration profiles and Configured systems in the provider.
Red Hat Satellite 6
Satellite 6 is a subscription and system management tool that provides a way to provision hosts (both virtual and bare metal) and configure them using a set of Puppet modules. ManageIQ provides functionality to integrate with a Red Hat Satellite 6 server and take advantage of its features. This includes:
-
Monitoring the inventory of your Red Hat Satellite 6 server, including independent hosts and hosts provisioned using hostgroups.
-
Reprovisioning existing bare metal system hosts to new host groups.
-
Applying ManageIQ policy tags to hosts.
Defining the Workflow
This section uses the following workflow:
-
Add Red Hat Satellite 6 server details to ManageIQ.
-
Refresh the state of your Red Hat Satellite 6 provider in ManageIQ.
-
Select an existing bare metal host from Red Hat Satellite 6 for reprovisioning.
-
Apply policy tags to Red Hat Satellite 6 hosts.
Defining the Hostgroup Hierarchy
ManageIQ displays the Red Hat Satellite 6 infrastructure in a host group and host relationship. A host group defines a set of default values that hosts inherit when placed in that group. Hosts can belong to only one host group, but host groups can be nested in hierarchies. You can create a “base” or “parent” host group that represents all hosts in your organization, and then create nested or “child” host groups under that parent to provide specific settings.
Adding a Satellite 6 Provider
To start provisioning bare metal machines, you need at least one Red Hat Satelllite 6 provider added to ManageIQ.
-
Browse to menu: Configuration > Management.
-
Select menu: Configuration > Add a new Provider.
-
Enter a Name for the provider.
-
Enter a URL for the provider. This is the root URL for the Satellite 6 server and can be either an IP address or a hostname. For example,
http://satellite6.example.com. -
Select Verify Peer Certificate to use encrypted communication with the provider. This requires the SSL certificates from your Red Hat Satellite 6 provider.
-
Enter a Username for a user on the provider. Ideally, this would be a user in Satellite 6 with administrative access.
-
Enter a Password, and then enter it again in Confirm Password.
-
Click Validate to test your connection with the Red Hat Satellite 6 server.
-
Click Add to confirm your settings and save the provider.
ManageIQ saves the Satellite 6 provider in its database and triggers a refresh of resources detected in the provider.
Triggering a Refresh of a Satellite 6 Provider
Your Satellite 6 provider can still create new hosts independently of ManageIQ. Your ManageIQ appliance detects these changes after an automatic refresh period. However, you can trigger a manual refresh to avoid waiting for the automatic refresh.
-
Navigate to menu:Configuration[Management].
-
Select your Red Hat Satellite 6 provider using the checkbox, and click menu:Configuration[Refresh Relationships and Power States]. This triggers the refresh.
-
When the refresh is complete, select the Red Hat Satellite 6 provider to check the updated list of hosts groups in the provider.
Displaying Red Hat Satellite 6 Contents
ManageIQ provides two methods for viewing the contents of a Red Hat Satellite 6 provider:
-
Providers - This presents the Red Hat Satellite 6 contents as a hierarchy of host groups belonging to a provider, and then individual hosts belonging to each provider.
-
Configured Systems - This presents a list of all hosts on your Red Hat Satellite 6 server. This also provides a method to apply predefined filters to organized specific machines.
Change between these two views using the accordion menu on the left of the user interface.
Reprovisioning a Bare Metal Host
This procedure provides an example of reprovisioning an existing bare metal system into a new hostgroup. For this example, your Red Hat Satellite 6 environment requires the following:
-
An existing bare metal system stored as a host object in your Red Hat Satellite 6 server. This system can be one of the following:
-
A standalone system previously provisioned without a host group.
-
A system previously provisioned using a host group.
-
-
A target host group. This host group contains the system configuration to apply to the host when reprovisioning it. This includes:
-
A new operating system installation, including a new partition table.
-
A new networking configuration that the Red Hat Satellite 6 server defines and manages.
-
Registration to any Red Hat subscriptions and repositories assigned to the host group.
-
Application of any Puppet modules assigned to the host group.
-
-
Browse to menu: Configuration > Management.
-
Select Configured Systems from the accordion menu on the left. This displays the system list.
-
Select one or more hosts to reprovision.
-
Select menu:Lifecycle[Provision Configured Systems].
-
Under the Request tab, enter the following details:
-
E-Mail address
-
First Name
-
Last Name
-
This form also contains optional fields for users to enter a plain text Note to inform ManageIQ administrators of any special details, and a field to provide a manager’s name in case administrators require approval from a user’s manager.
-
-
Select the Purpose tab and select any ManageIQ policy tags that apply to the system.
-
Select the Catalog tab. This screen displays the list of chosen machines to reprovision and their current details. Select a target host group from the Configuration Profile list. ManageIQ communicates with Red Hat Satellite to apply the configuration from this host group to the selected host and reprovision the system.
-
Select the Customize tab. This screen displays some customizable fields for the selected system. You can change the Root Password or change the Hostname and IP Address. Note that these fields are optional, because the host group in Red Hat Satellite 6 contains this information. The fields here will override the settings from the host group.
Provisioning bare metal systems still requires access to the network that Red Hat Satellite 6 manages. This is because Red Hat Satellite controls PXE booting, kickstarts, and Puppet configuration for bare metal systems. Ensure the IP address you enter in ManageIQ can access a DHCP service that Red Hat Satellite 6 provides either through the main server or through a Red Hat Satellite 6 Capsule server. -
Select the Customize tab. This screen allows you to either launch the provisioning process immediately on approval or using a schedule. Click Schedule to show the date and time fields used to schedule the provisioning.
-
Click Submit.
Depending on the request settings on your ManageIQ appliance, this provisioning request might require approval from an administrator. If not, the provisioning request launches depending on your choice for the schedule.
Note:
Previously provisioned hosts might require manual selection of PXE boot from the boot menu, otherwise they might boot to hard disk and not reprovision.
Tagging a Bare Metal Host
ManageIQ can also control policy settings of bare metal systems from Red Hat Satellite 6 through tagging. Tagging attaches levels of metadata to help define the policy rules required for a set of systems.
-
Navigate to menu:Configuration[Management].
-
Select Configured Systems from the accordion menu on the left. This displays the system list.
-
Select one or more hosts to tag.
-
Select menu:Policy[Edit Tags].
-
Under Tag Assignment, select a tag from Select a customer tag to assign and then choose a value from Select a value to assign. For example, you can tag this system as located in Chicago by selecting
Locationas the tag andChicagoas the value. Once selected, the user interface automatically adds this tag and value to the table below. -
Click Save.
The bare metal system is now configured with a set of policy tags.
Automation Management Providers
In ManageIQ, an automation management provider is a management tool that integrates with ManageIQ to simplify automation operations for your resources. This chapter describes the automation management providers that you can use with ManageIQ, and how to work with them.
ManageIQ provides automation management features through the following:
Automate enables real-time, bi-directional process integration. This provides you with a method to implement adaptive automation for management events and administrative or operational activities.
Ansible integration delivers out-of-the-box support for backing service, alert and policy actions using Ansible playbooks. Sync your existing playbook repositories with ManageIQ, add credentials to access providers, and create service catalog items for actions ranging from creating and retiring VMs, updating security software, or adding additional disks when space runs low.
Ansible Tower is a management tool integrated with ManageIQ, designed to help automate infrastructure operations utilizing existing Ansible Tower providers in your inventory. ManageIQ allows you to execute Ansible Tower jobs using service catalogs and Automate. Using Ansible Tower, you can schedule Ansible playbook runs and monitor current and historical results, allowing for troubleshooting or identification of issues before they occur.
Ansible
Ansible integrates with ManageIQ to provide automation solutions, using playbooks, for Service, Policy and Alert actions. Ansible playbooks consist of series of plays or tasks that define automation across a set of hosts, known as the inventory.
Ranging from simple to complex tasks, Ansible playbooks can support cloud management:
-
Services - allow a playbook to back a ManageIQ service catalog item.
-
Control Actions - ManageIQ policies can execute playbooks as actions based on events from providers.
-
Control Alerts - set a playbook to launch prompted by a ManageIQ alert.
Ansible is built into ManageIQ so there is nothing to install. The basic workflow when using Ansible in ManageIQ is as follows:
-
Enable the Embedded Ansible server role.
-
Add a source control repository that contains your playbooks.
-
Establish credentials with your inventory.
-
Back your services, alerts and policies using available playbooks.
Enabling the Embedded Ansible Server Role
In ManageIQ, the Embedded Ansible role is disabled by default. Enable this server role to utilize Ansible Automation Inside.
Note:
Configure your ManageIQ appliance network identity (hostname/IP address) before enabling the Embedded Ansible server role.
Restart the evmserverd service on the appliance with the enabled Embedded Ansible server role after making any changes to the hostname or IP address.
-
Browse to the settings menu, then Configuration → Settings.
-
Select the desired server under Zones.
-
Set the Server Role for Embedded Ansible to On.
Verifying the Embedded Ansible Worker State
Verify that the Embedded Ansible worker has started to utilize its features.
-
Browse to the settings menu, then Configuration → Diagnostics and click on the desired server.
-
Click on the Workers tab.
A table of all workers and current status will appear from which you can confirm the state of your embedded Ansible worker.
Adding a Playbook Repository
Add a repository so that ManageIQ can discover and make available your playbooks.
-
Browse to menu: Automation > Ansible > Repositories.
-
Click Add.
-
Provide a Repository Name in the Name field.
-
Add a description for the repository in the Description field.
-
Select an SCM Type from the drop-down menu.
-
Add a URL or IP Address for the repository.
-
Select the appropriate SCM Credentials from the drop-down menu.
-
Provide a branch name in the SCM Branch field.
-
Check the appropriate box for any SCM Update Options.
-
Click Add.
Once you have synced a repository, its playbooks will become available to ManageIQ.
Refreshing Repositories
ManageIQ allows you to refresh a targeted playbook repository or all repositories in your inventory to ensure your playbooks are current.
Refresh a targeted repository:
-
Browse to menu: Automation > Ansible > Repositories.
-
Click on a repository.
-
Click Configuration, then
 (Refresh this
Repository).
(Refresh this
Repository).
Alternately, you can refresh some or all repositories from the list view:
-
Browse to menu: Automation > Ansible > Repositories.
-
Check those repositories to refresh. Click Check All to select all repositories.
-
Click Configuration, then
 (Refresh Selected Ansible Repositories).
(Refresh Selected Ansible Repositories).
Credentials
Credentials are utilized by ManageIQ for authentication when running Ansible playbooks against machines, synchronizing with inventory sources, and importing project content from a version control system.
Adding Credentials
ManageIQ can store credentials used by playbooks. Credentials saved in ManageIQ are matched and executed with a playbook when run.
-
Browse to menu: Automation > Ansible > Credentials.
-
Click Configuration, then
 (Add a New
Credential).
(Add a New
Credential). -
Provide a Name for the credential.
-
Select the Credential Type. Additional fields will appear depending on the type chosen.
-
Click Add.
Credential Types
Each credential type used by ManageIQ is detailed in the following sections.
Machine
Machine credentials enable ManageIQ to invoke Ansible on hosts under your management. Just like using Ansible on the command line, you can specify the SSH username, optionally provide a password, an SSH key, or a key password. They define SSH and user-level privilege escalation access for playbooks, and are used when running playbooks on a remote host.
-
Username: The username to be used for SSH authentication.
-
Password: The actual password to be used for SSH authentication.
-
SSH Private Key: Copy or drag-and-drop the SSH private key for the machine credential.
-
Private Key Passphrase: If the SSH Private Key used is protected by a password, you can configure a Key Password for the private key.
-
Privilege Escalation: Specifies the type of escalation privilege to assign to specific users. Options include sudo, su, pbrun, pfexec.
-
Privilege Escalation Username: Enter the username to use with escalation privileges on the remote system.
-
Privilege Escalation Password: Enter the actual password to be used to authenticate the user via the selected privilege escalation type on the remote system.
-
Vault Password: Ansible Vault credentials have only the Vault Password attribute that may be configured.
Note:
For more information on Ansible Vault, see Using Vault in playbooks.
Network
Network credentials are used by Ansible networking modules to connect to and manage networking devices.
Network credentials have several attributes that may be configured:
-
Username: The username to use in conjunction with the network device.
-
Password: The password to use in conjunction with the network device.
-
Authorize: Select this from the Options field to add an Authorize password which signs the RSA key with a password.
-
Authorize password: If Authorize is checked, enter a password in the Authorize Password field.
-
SSH Key: Copy or drag-and-drop the actual SSH Private Key to be used to authenticate the user to the network via SSH.
-
Private key passphrase: The actual passphrase for the private key to be used to authenticate the user to the network via SSH.
SCM
SCM (source control) credentials are used with Projects to clone and update local source code repositories from a remote revision control system such as Git, Subversion, or Mercurial.
Source Control credentials have several attributes that may be configured:
-
Username: The username to use in conjunction with the source control system.
-
Password: The password to use in conjunction with the source control system.
-
Private key passphrase: If the SSH private key used is protected by a passphrase, you may configure a key passphrase for the private key.
-
Private Key: Copy or drag-and-drop the actual SSH Private Key to be used to authenticate the user to the source control system via SSH.
Amazon
Selecting this credential type enables synchronization of cloud inventory with Amazon Web Services.
-
Access Key: User credentials that allow for programmatic calls to Amazon Web Services.
-
Secret Key: The secret key that corresponds to the user access key.
-
STS Token: Token generated by Amazon Web Services Security Token Service.
Azure Classic (deprecated)
Selecting this credential type enables synchronization of cloud inventory with Microsoft Windows Azure Classic.
Microsoft Azure credentials have several attributes to configure:
-
Subscription ID: The Subscription UUID for the Microsoft Azure Classic account.
-
Management Certificate: The PEM file that corresponds to the certificate you uploaded in the Microsoft Azure Classic console.
Azure
Selecting this credential type enables synchronization of cloud inventory with Microsoft Azure.
Microsoft Azure credentials have several attributes to configure:
-
Username: The username to use to connect to the Microsoft Azure account.
-
Password: The password to use to connect to the Microsoft Azure account.
-
Subscription ID: The Subscription UUID for the Microsoft Azure account.
-
Tenant ID: The Tenant ID for the Microsoft Azure account.
-
Client Secret: The Client Secret for the Microsoft Azure account.
-
Client ID: The Client ID for the Microsoft Azure account.
OpenStack
Selecting this credential type enables synchronization of cloud inventory with Red Hat OpenStack Platform.
OpenStack credentials have several attributes that may be configured:
-
Username: The username to use to connect to OpenStack.
-
Password (API Key): The password or API key to use to connect to OpenStack.
-
Host (Authentication URL): The host to be used for authentication.
-
Project (Tenant Name): The Tenant name or Tenant ID used for OpenStack. This value is usually the same as the username.
-
Domain name: The FQDN to be used to connect to OpenStack.
Rackspace
Selecting this credential type enables synchronization of cloud inventory with Rackspace.
Rackspace credentials have the following attributes that may be configured:
-
Username: The username to use to connect to vCenter.
-
API Key: The public key related to the administrator ID.
Red Hat Virtualization
Selecting this credential type enables synchronization of cloud inventory with Red Hat Virtualization.
Red Hat Virtualization credentials have several attributes that may be configured:
-
Username: The username to use to connect to Red Hat Virtualization.
-
Password: The password to use to connect to Red Hat Virtualization.
-
Host (Authentication URL): The host to be used for authentication.
- Enter in **Host** the Red Hat Virtualization provider URL, followed by the path `/ovirt_engine/api`. Example: `https://your.rhv.com/ovirt_engine/api` - See [Ansible Roles](https://access.redhat.com/documentation/en-us/red_hat_virtualization/4.1/html/administration_guide/chap-automating_rhv_configuration_using_ansible#Ansible_Roles) for more information on Ansible Roles available for Red Hat Virtualization.
Satellite 6
Selecting this credential type enables synchronization of cloud inventory with Red Hat Satellite 6.
Satellite credentials have several attributes that may be configured:
-
Username: The username to use to connect to Satellite 6.
-
Password: The password to use to connect to Satellite 6.
-
Satellite 6 Host: The Satellite 6 URL or IP address to connect to.
VMware
Selecting this credential type enables synchronization of inventory with VMware vCenter.
Important:
If both ManageIQ and a VMware provider are located in the same IPv6-only network, use a DNS-resolvable hostname for the VMware provider in the vCenter Host field when adding credentials.
VMware credentials have several attributes that may be configured:
-
Username: The username to use to connect to vCenter.
-
Password: The password to use to connect to vCenter.
-
vCenter Host: The vCenter hostname or IP address to connect to.
Note:
If the VMware guest tools are not running on the instance, VMware inventory sync may not return an IP address for that instance.
Tagging Ansible Playbooks, Repositories, and Credentials
Apply tags to Ansible playbooks, repositories, and credentials to categorize them. Tagging enables administrators to limit users to view those Ansible elements that have been enabled for that set of user permissions.
Adding Tags to Ansible Playbooks
-
Navigate to menu:Automate[Ansible > Playbooks].
-
Select the checkboxes for the Ansible playbooks to tag.
-
Click
 (Policy), and then
(Policy), and then  (Edit Tags).
(Edit Tags). -
Select a customer tag to assign from the first list.
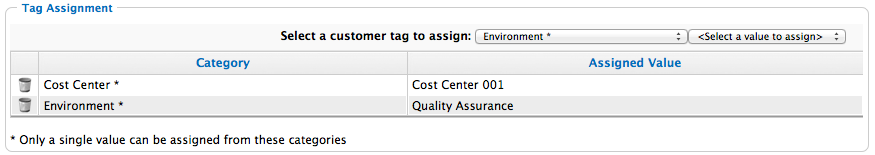
-
Select a value to assign from the second list.
-
Click Save.
Adding Tags to Ansible Repositories
-
Navigate to menu:Automate[Ansible > Repositories].
-
Select the checkboxes for the Ansible repositories to tag.
-
Click
 (Policy), and then
(Policy), and then  (Edit Tags).
(Edit Tags). -
Select a customer tag to assign from the first list.

-
Select a value to assign from the second list.
-
Click Save.
Adding Tags to Ansible Credentials
-
Navigate to menu:Automate[Ansible > credentials].
-
Select the checkboxes for the Ansible credentials to tag.
-
Click
 (Policy), and then
(Policy), and then  (Edit Tags).
(Edit Tags). -
Select a customer tag to assign from the first list.

-
Select a value to assign from the second list.
-
Click Save.
Optimizing Ansible Playbooks for ManageIQ
Ansible is a simple model-driven configuration management, multi-node deployment, and remote-task execution system. When designing playbooks for use with ManageIQ it is helpful to utilize solutions within the playbook itself to ensure optimal implementation of playbook-backed services or automated processes.
This section is intended to complement the existing documentation on Ansible playbooks and guide administrators through optimizing playbooks for use with ManageIQ.
Installing Roles on an Embedded Ansible Appliance
Roles are ways of automatically loading certain variable files, tasks, and handlers based on a known file structure. Grouping content by roles also allows easy sharing of roles with other users. Install roles on a ManageIQ appliance with the Embedded Ansible server role activated to optimize playbooks.
When using this role in a playbook on a ManageIQ
appliance, add an empty roles directory at the root of the playbook.
In the roles directory, include a requirements.yml file with the
following contents:
---
- src: <ansible-galaxy-role>
ManageIQ will automatically install the role once it sees
the requirements.yml file in the playbook.
Ansible Service Linking
ManageIQ provides a module allowing inventoried resources such as
virtual machines created using Ansible playbooks to link back to the
services used to generate them. During service ordering of a playbook
the add_provider_vms module will allow the playbook to connect back to
the worker appliance and identify the provider resources it was
responsible for generating. Once linked, the newly generated resources
are available to ManageIQ’s life cycle management
features.
Linking VMs back to the service that created it requires implementing the following tasks in the playbook used for provisioning:
-
Create a resource and register it.
-
Link the service using the
add_provider_vmsmethod to the newly created resource.
Example: Linking a virtual machine to a service
In the following playbook task examples, a virtual machine is deployed to Amazon EC2 and linked back to the service. Examples are provided for linking the resource to its service by both an href slug and as an object.
Note:
-
This example utilizes the `syncrou.manageiq-vmdb` role. This role allows ManageIQ users to modify and/or change VMDB objects using an Ansible playbook. For information on implementing and utilizing roles when writing Ansible playbooks for ManageIQ, see Installing Ansible Roles.
-
For more information on Ansible Galaxy and roles, see the Ansible Galaxy documentation.
-
Note the provider ID in order to successfully link to the service.
-
Create and register the resource.
- name: Create Ec2 Instance ec2: key_name: "" instance_tags: {Name: ""} group_id: "" instance_type: "" region: "" image: "" wait: yes count: 1 vpc_subnet_id: "" assign_public_ip: yes register: ec2 -
Call the
add_provider_vmsmethod as an action to link to the service via an href slug or an object.- name: Service Linking via an href slug manageiq_vmdb: href: "href_slug::services/80" action: add_provider_vms data: uid_ems: - "" provider: id: 24 - name: Service Linking via an object manageiq_vmdb: vmdb: "" action: add_provider_vms data: uid_ems: - "" provider: id: 24
Modifying the Automate Workspace Using the manageiq-automate Role.
The manageiq-automate role allows users of ManageIQ Automate to
modify and add to the automate workspace via an Ansible playbook.
Note:
When using this role in a playbook on a ManageIQ appliance with
Embedded Ansible activated, add an empty roles directory at the root
of the playbook. In the roles directory, include a requirements.yml
file with the following contents:
---
- src: syncrou.manageiq-automate
ManageIQ will automatically install the role once it sees
the requirements.yml file in the playbook.
Role Variables
The manageiq_automate role employs the following variables when
implemented in a playbook run on a ManageIQ appliance.
Variables are defined in defaults/main.yml and vars/main.yml.
auto_commit: By default is set to True. If set to False it will not
auto commit back to ManageIQ each call to a set_ method
in the manageiq_automate module.
manageiq_validate_certs: By default is set to True. If passed in
via extra_vars or assigned in the playbook variables then the lookup
will allow self-signed certificates to be used when using SSL REST API
connection URLs.
Example Playbook
The example below utilizes the manageiq-automate role. Using variable
substitution, playbook tasks retrieve method parameters which are then
used to modify object attributes. A final task uses the set_retry
module to update the retry interval.
- name: Siphon Method Parameters into an object
hosts: localhost
connection: local
vars:
- auto_commit: True
- object: root
- interval: 600
gather_facts: False
roles:
- syncrou.manageiq-automate
tasks:
- name: "Get the list of Method Parameters"
manageiq_automate:
workspace: ""
get_method_parameters: yes
register: method_params
- name: "Set attributes"
manageiq_automate:
workspace: ""
set_attributes:
object: ""
attributes: ""
- name: Set Retry
manageiq_automate:
workspace: ""
set_retry:
interval: ""
Callbacks in Multiple Appliance Environments
In a ManageIQ multiple appliance environment, enable the Embedded
Ansible server role on a dedicated ManageIQ appliance. Add
store_session:sql to Ansible playbooks to ensure successful callbacks
to ManageIQ appliances in a multiple appliance
environment.
Ansible Tower
Ansible Tower is a management tool integrated with ManageIQ, designed to help automate infrastructure operations. ManageIQ allows you to execute Ansible Tower jobs or workflows using service catalogs and Automate. No custom configuration or Ruby scripting is needed in ManageIQ, as configuration is done in Ansible Tower using playbooks.
You can use the large library of existing Ansible playbooks as ManageIQ state machines to automate tasks such as deployments, backups, package updates, and maintenance in your ManageIQ environment. This can be particularly useful for quickly applying changes across large environments with many virtual machines or instances.
Using Ansible Tower, you can schedule Ansible playbook runs and monitor current and historical results, allowing for troubleshooting or identification of issues before they occur.
ManageIQ supports Ansible Tower API v2 provider integration.
Working with an Ansible Tower Provider
The basic workflow when using ManageIQ with an Ansible Tower provider is as follows:
-
Create an Ansible playbook which performs a specific task.
-
A new Ansible Tower job template is created from the playbook (or workflow template created from disparate jobs), which is then retrieved by ManageIQ.
-
From the Ansible Tower job or workflow template, create a new catalog item in ManageIQ, optionally with a service dialog that allows the user to enter parameters if needed.
-
The user orders the service from the ManageIQ user interface, and fills out any additional arguments (for example, limiting the task to run on a specific set of virtual machines).
-
The job or workflow executes.
Note:
-
For more information on Ansible playbooks, see the Ansible playbook documentation.
-
For more information on worklows, see Workflows in the Ansible Tower User Guide.
Adding an Ansible Tower Provider
To access your Ansible Tower inventory from ManageIQ, you must add Ansible Tower as a provider.
Note:
-
Ensure ENABLE HTTP BASIC AUTH is set to On in the Ansible Tower configuration settings before adding the provider. See Tower Configuration in the Ansible Tower Administration Guide.
-
A trailing slash is not required at the end of the Ansible Tower provider URL. Adding the trailing slash to the provider URL may result in a validation error.
-
Browse to menu: Automation > Ansible Tower > Explorer and click on the Providers accordion tab.
-
Under Configuration, click
 Add a new Provider.
Add a new Provider. -
In the Add a new Provider area:
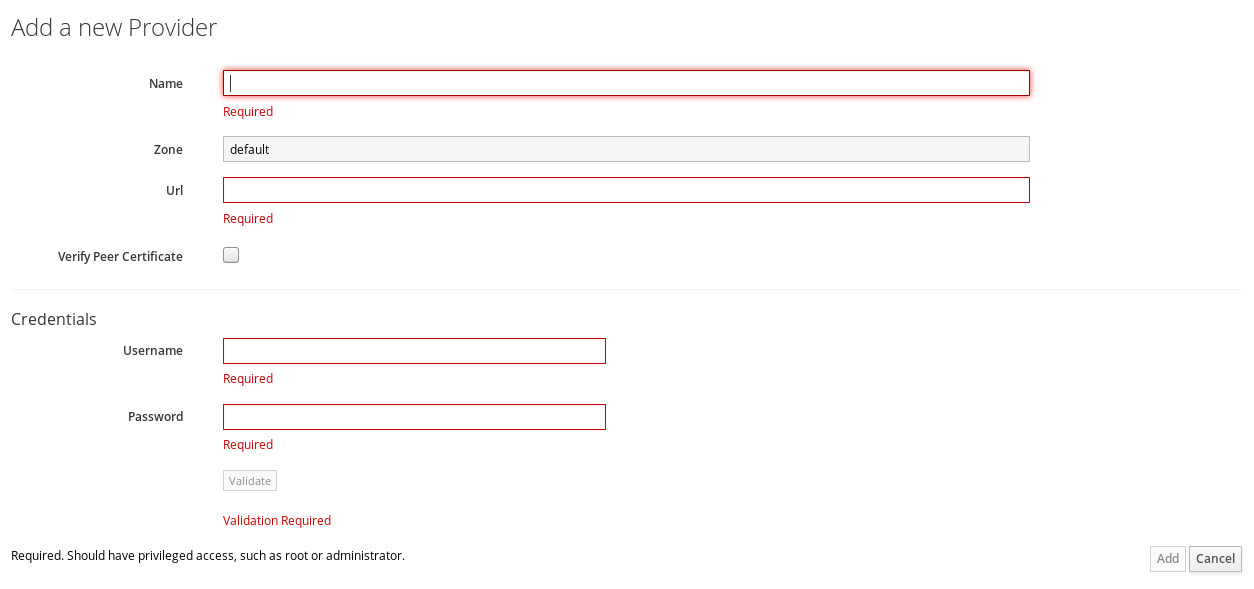
-
Enter a Name for the new provider.
-
Add a Zone for the provider.
-
Enter the URL location or IP address to the Ansible Tower server. Add a trailing slash to the end of the Ansible Tower provider URL.
-
-
Select the Verify Peer Certificate checkbox if desired.
-
In the Credentials area, provide the Username and Password, and Confirm Password.
-
Click Validate to verify credentials.
-
Click Add.
After adding the Ansible Tower provider, refresh its relationships and power states in order to view the current inventory.
Refreshing an Ansible Tower Provider
Refresh relationships of all items related to an existing Ansible Tower configuration management provider including inventory, hosts, virtual machines, and clusters.
You can refresh inventory from ManageIQ, or by enabling the Update on Launch option for inventory groups in Ansible Tower. The Update on Launch option allows Ansible Tower to automatically update inventory using a dynamic inventory script before launching an Ansible Tower job from a playbook. See the Ansible Tower documentation for more information.
Important
It can take a long time to retrieve information from providers containing many virtual machines or instances. The Ansible Tower dynamic inventory script can be modified to limit updates to specific items and reduce refresh time.
To refresh an Ansible Tower provider’s inventory in ManageIQ:
-
Browse to menu: Automation > Ansible Tower > Explorer and click the Providers accordion tab.
-
Select the checkboxes for the Ansible Tower providers to refresh under All Ansible Tower Providers.
-
Click Configuration, and then
 (Refresh Relationships and Power States).
(Refresh Relationships and Power States). -
Click OK.
ManageIQ then queries the Ansible Tower API and obtains an inventory of all available hosts, job and workflow templates.
Viewing Ansible Tower Providers and Inventory
ManageIQ automatically updates its inventory from Ansible Tower. This includes system groups (known as Inventories in Ansible Tower), basic information about individual systems, and available Ansible Tower job or workflow templates to be executed from the service catalog or Automate.
Note:
To view and access Ansible Tower inventories and job or workflow templates in ManageIQ, you must first create them in Ansible Tower.
To view a list of Ansible Tower providers and inventory:
-
Browse to menu: Automation > Ansible Tower > Explorer.
-
select the Providers accordion menu to display a list of All Ansible Tower Providers.
-
Select your Ansible Tower provider to expand and list the inventory groups on that Ansible Tower system. The inventory groups can be expanded to view the systems contained within each group, as well as configuration details for these systems.
Similarly, all discovered job and workflow templates are accessed under the provider by expanding the menu: Automation > Ansible Tower > Explorer and click the Templates accordion menu.
Viewing Ansible Tower Configured Systems
To view the systems in your Ansible Tower inventory:
-
Browse to menu: Automation > Ansible Tower > Explorer and click Configured Systems.
-
Under All Ansible Tower Configured Systems, select Ansible Tower Configured Systems to display a list.
Executing an Ansible Tower Job or Workflow Template from a Service Catalog
You can execute an Ansible Tower playbook from ManageIQ by creating a service catalog item from an Ansible Tower job or workflow template.
Important:
You must first create the job or workflow template in Ansible Tower. The job or workflow templates are automatically discovered by ManageIQ when refreshing your Ansible Tower provider’s inventory.
First, create a catalog:
-
Browse to menu: Services > Catalogs and click Catalog Items.
-
Click Configuration, then
 (Add a New Catalog)
(Add a New Catalog) -
Enter a Name and Description for the catalog.
-
Click Add.
Then, create an Ansible Tower service catalog item:
-
Browse to menu: Automation > Ansible Tower > Explorer, then click the Templates according menu.
-
Click Ansible Tower Templates and select an Ansible Tower job or workflow template.
-
Click Configuration, then
 (Create Service Dialog from this Template).
(Create Service Dialog from this Template). -
Enter a Service Dialog Name (for example, ansible_tower_job)and click Save.
-
Browse to menu: Services > Catalogs and click Catalog Items.
-
Click Configuration, then
 (Add a New Catalog Item) to create a new catalog item with the following details, at minimum:
(Add a New Catalog Item) to create a new catalog item with the following details, at minimum:-
For Catalog Item type, select Ansible Tower.
-
Enter a Name for the service catalog item.
-
Select Display in Catalog.
-
In Catalog, select the catalog you created previously.
-
In Dialog, select the service dialog you created previously (in this example, ansible_tower_job). To ask the user to enter extra information when running the task, Service Dialog must be selected. A dialog is required if Display in Catalog is chosen.
-
In Provider, select your Ansible Tower provider. This brings up the Ansible Tower Template option and configures the Provisioning Entry Point State Machine automatically.
-
Add configuration information for Reconfigure Entry Point and Retirement Entry Point as applicable.
-
Select your desired Ansible Tower Template from the list. Generally, this is the Ansible Tower job or workflow template previously used to create the service dialog.
-
-
Click Add. The catalog item you created will appear in the All Service Catalog Items list.
To execute the Ansible Tower job:
-
Browse to menu: Service > Catalogs and click on Service Catalogs then click Ansible Tower catalog.
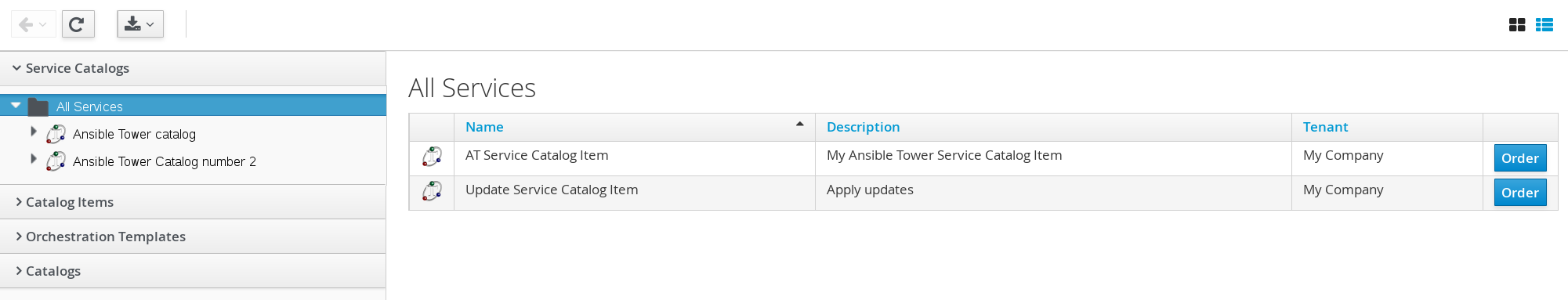
-
Click Order for the catalog item.
-
Enter any variables requested and click Submit.
ManageIQ takes you to the Requests queue page and show the status of the job.
The service item’s details can be viewed in menu: Services > My Services in ManageIQ.
Note:
Instead of running a single job at a time, multiple service catalog items can also be grouped together as a catalog bundle to create one deployment with multiple job templates. See Catalogs and Services in Provisioning Virtual Machines and Hosts for more information.
Executing an Ansible Tower Job Using a Custom Automate Button
ManageIQ can execute Ansible Tower jobs on virtual machines or instances using custom buttons in Automate.
Ansible Tower jobs can either be non-customizable, which do not require any extra configuration from the user, or alternatively, they can allow the user to specify a parameter (for example, a package name to install). In Ansible Tower jobs containing a dialog, ManageIQ accepts additional information from the user and adds it to the appropriate API call in Automate, and then sends it into Ansible Tower.
Prerequisites.
Before creating an Automate button to execute an Ansible Tower job, the following must be configured:
-
An Ansible playbook in Ansible Tower. See the Ansible Tower documentation for instructions.
-
Ansible Tower must be able to reach virtual machines or instances deployed by ManageIQ at the IP level.
-
The virtual machine template must have the Ansible Tower environment’s public SSH key injected. For cloud instances,
cloud-initcan be used and the public SSH key can be passed without rebuilding the image. -
Any dynamic inventory scripts used must be configured to return the virtual machine names exactly as they are stored in ManageIQ, without the UUID appended.
Executing an Ansible Tower Job using a Custom Automate Button.
To configure a custom button to execute an Ansible Tower job on a virtual machine or instance, first create the button:
-
Browse to menu: Automation > Automate > Customization.
-
Click the Buttons accordion menu.
-
Click menu: VM and Instance > Unassigned Buttons. This configures the button to run on virtual machines or instances.
-
Click Configuration, then click
 (Add a new Button).
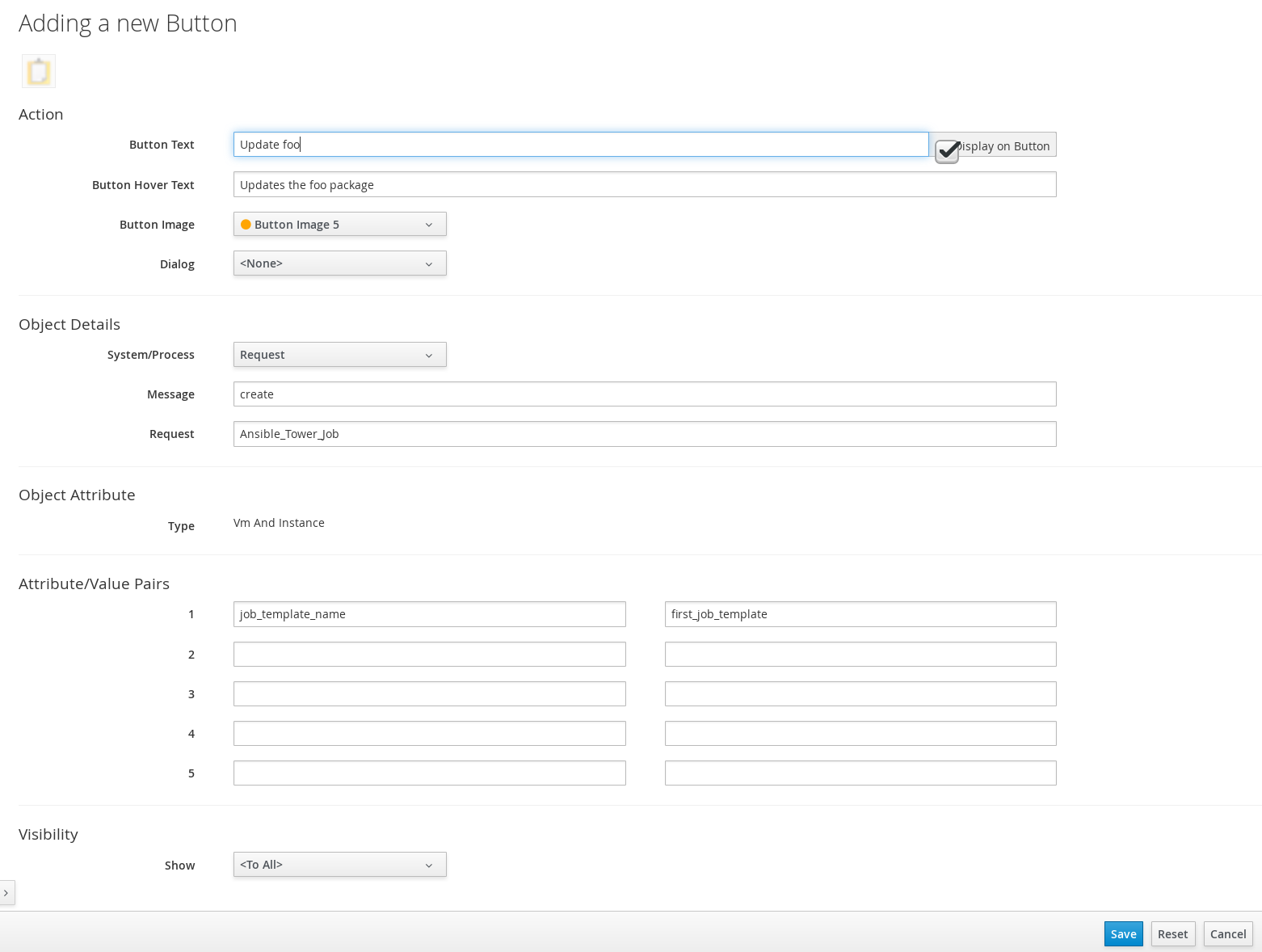
(Add a new Button).-
In the Adding a new Button screen, configure the Action parameters as desired. Dialog can be left blank if the playbook does not require extra variables. To ask the user to enter extra information when running the task, Service Dialog must be selected.
-
Configure Object Details fields with the following request details:
-
For System/Process, select Request.
-
For Message, enter create.
-
For Request, enter Ansible_Tower_Job.
-
-
Configure Attribute/Value Pairs with the following parameters:
- job_template_name is the Ansible Tower job template name to associate with the button. The job_template_name field is mandatory; other parameters are provided by the Tower job dialog.
-
Configure Visibility to all users, or limit visibility by role as desired.
-
Click Add.
-
If you do not have an existing button group to assign the new button to, create a new button group:
-
From menu: Automation > Automate > Customization, browse to menu: Buttons and click VM and Instance > Add a new Button Group, and configure the following:
-
Configure Basic Info as desired. For example, name the button group
VM Actions. -
In Assign Buttons, select the button you just created from the Unassigned list and click
 to
assign it to Selected.
to
assign it to Selected.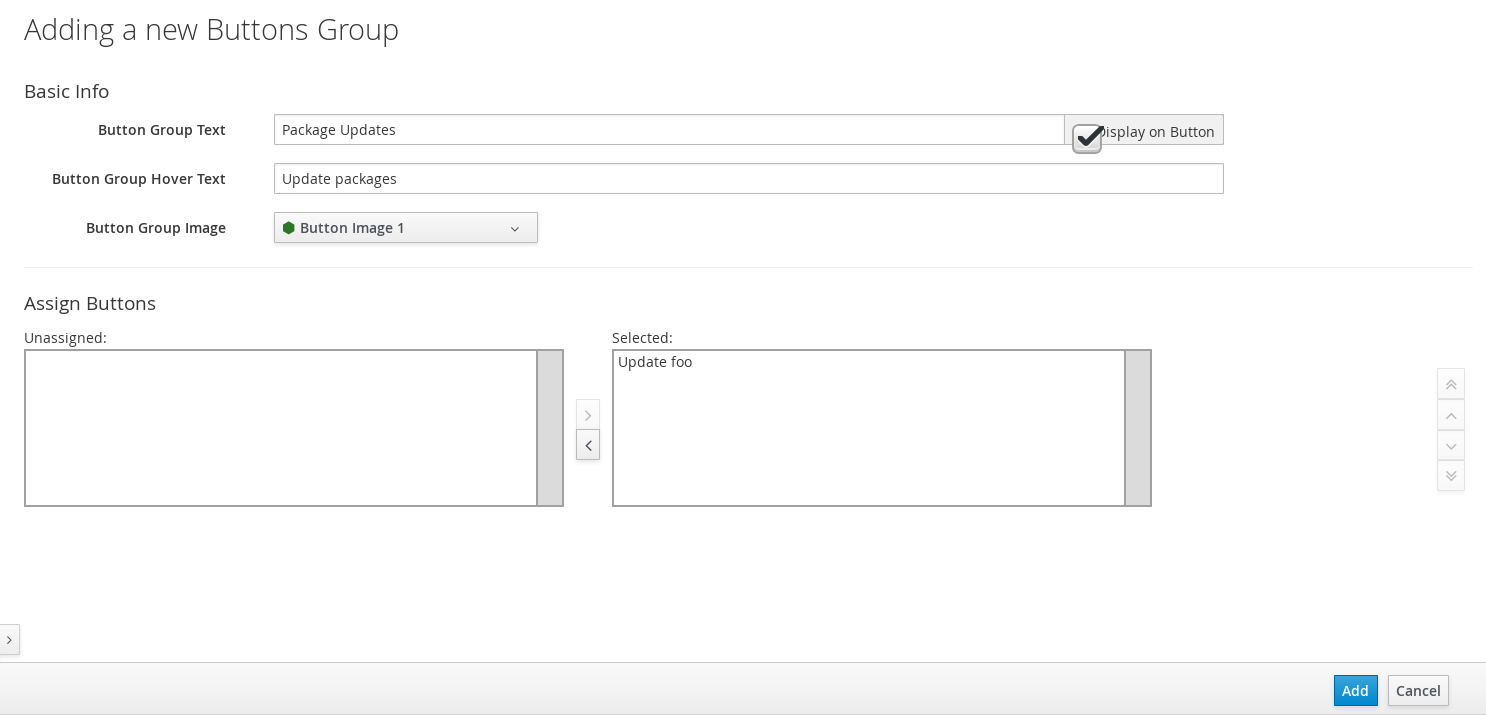
-
Click Add.
-
To assign the button to an existing button group:
-
Browse to menu: Buttons > VM and Instance > VM Actions > Edit this Button Group.
-
In Assign Buttons, select the button you just created from the Unassigned list and click
 to assign it to Selected.
to assign it to Selected. -
Click Add.
To use the button to run an Ansible Tower job on a virtual machine:
-
Browse to menu: Compute > Infrastructure > Virtual Machines.
-
Select the virtual machine to run the Ansible Tower job template on.
-
Click the VM Actions button to show the button you created, and click the button from the list to run the Ansible Tower job template.
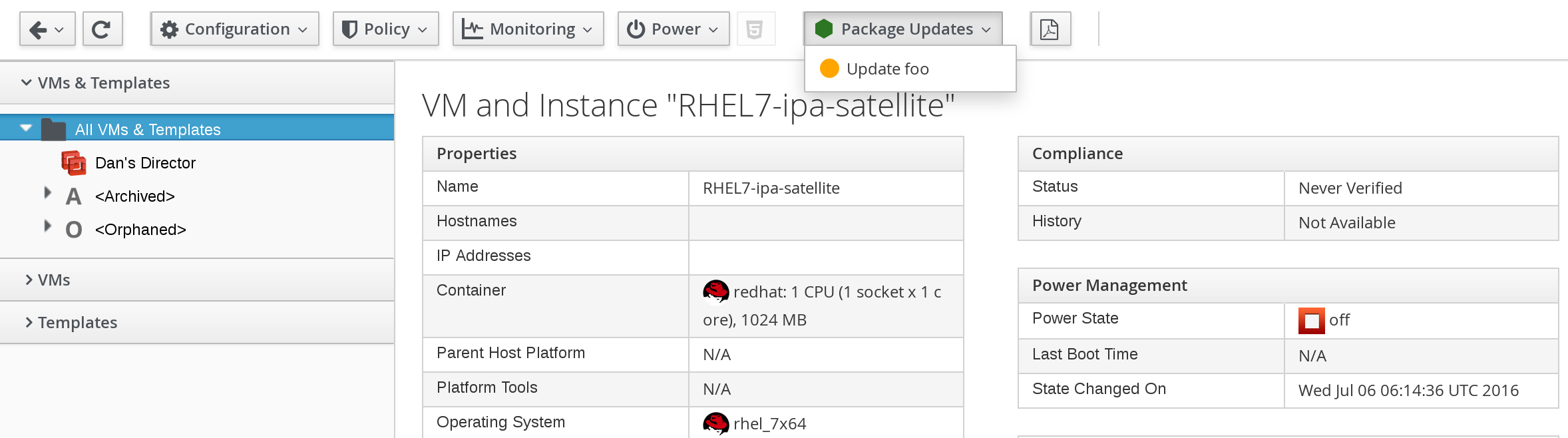
-
Click Submit to execute the job.
ManageIQ then confirms the job has been executed.
If you selected a service dialog to run when creating the button, ManageIQ will then prompt you to enter variables to complete the task. After entering your desired parameters, ManageIQ takes you to the Requests page.
The service item’s details can be viewed in menu: Services > My Services in ManageIQ.
Cloud Providers
In ManageIQ, a cloud provider is a cloud computing environment that you can add to a ManageIQ appliance to manage and interact with the resources in that environment. This chapter describes the different types of cloud providers that you can add to ManageIQ, and how to manage them. Most cloud providers are added individually to ManageIQ. Additionally, Amazon EC2 and Azure cloud providers can be discovered automatically by ManageIQ.
The web interface uses virtual thumbnails to represent cloud providers. Each thumbnail contains four quadrants by default, which display basic information about each provider:

-
Number of instances
-
Management system software
-
Number of images
-
Authentication status
| Icon | Description |
|---|---|
 |
Validated: Valid authentication credentials have been added. |
 |
Invalid: Authentication credentials are invalid. |
 |
Unknown: Authentication status is unknown or no credentials have been entered. |
Provider authentication status
OpenStack Providers
Adding OpenStack Providers
ManageIQ supports operating with the OpenStack admin tenant.
When creating an OpenStack provider in ManageIQ, select the
OpenStack provider’s admin user because it is the default
administrator of the OpenStack admin tenant. When using the admin
credentials, a user in ManageIQ provisions into the admin
tenant, and sees images, networks, and instances that are associated
with the admin tenant.
Note:
In OpenStack, you must add admin as a member of all tenants that users want to access and use in ManageIQ.
See Cloud Tenants in Managing Infrastructure and Inventory for information on working with OpenStack tenants (projects) in ManageIQ.
When adding an OpenStack cloud or infrastructure provider, enable tenant mapping in ManageIQ to map any existing tenants from that provider.
This means ManageIQ will create new cloud tenants to match each existing OpenStack tenant; each new cloud tenant and its corresponding OpenStack tenant will have identical resource assignments (including user and role synchronization) with the exception of quotas. Tenant quotas are not synchronized between ManageIQ and OpenStack, and are available for reporting purposes only. You can manage quotas in ManageIQ but this will not affect the quotas created in OpenStack.
During a provider refresh, ManageIQ will also check for any changes to the tenant list in OpenStack. ManageIQ will create new cloud tenants to match any new tenants, and delete any cloud tenants whose corresponding OpenStack tenants no longer exist. ManageIQ will also replicate any changes to OpenStack tenants to their corresponding cloud tenants.
If you leave tenant mapping disabled, ManageIQ will not create cloud tenants or tenant object hierarchy from OpenStack.
Note:
You can set whether ManageIQ should use the Telemetry service or Advanced Message Queueing Protocol (AMQP) for event monitoring. If you choose Telemetry, you should first configure the ceilometer service on the overcloud to store events. See Configuring the Overcloud to Store Events for instructions.
For more information, see OpenStack Telemetry (ceilometer) in the Red Hat OpenStack Platform Architecture Guide.
Note:
To authenticate the provider using a self-signed Certificate Authority (CA), configure the ManageIQ appliance to trust the certificate using the steps in Using a Self-Signed CA Certificate before adding the provider.
-
Browse to menu: Compute > Clouds > Providers.
-
Click Configuration, then click
 (Add a New Cloud Provider).
(Add a New Cloud Provider). -
From the Type list, select OpenStack.
-
Enter a Name for the provider.
-
Select the appropriate Zone for the provider. By default, the zone is set to default.
Note:
For more information, see the definition of host aggregates and availability zones in OpenStack Compute (nova) in the Red Hat OpenStack Platform Architecture Guide.
-
Enter the OpenStack region in Provider Region.
-
(Optional) Select an associated Openstack Infra Provider
-
Select the appropriate API Version from the list. The default is
Keystone v2.If you select
Keystone v3, enter theKeystone V3 Domain IDthat ManageIQ should use. This is the domain of the user account you will be specifying later in the Default tab. If domains are not configured in the provider, enter default.Note:
Keystone API v3 is required to create cloud tenants on OpenStack cloud providers.
Note:
- With Keystone API v3, domains are used to determine administrative boundaries of service entities in OpenStack. Domains allow you to group users together for various purposes, such as setting domain-specific configuration or security options. For more information, see OpenStack Identity (keystone) in the Red Hat OpenStack Platform Architecture Guide.
- The provider you are creating will be able to see projects for the given domain only. To see projects for other domains, add it as another cloud provider. For more information on domain management in OpenStack, see Domain Management in the Red Hat OpenStack Platform Users and Identity Management Guide.
-
(Optional) Enable tenant mapping by toggling the Tenant Mapping Enabled option to Yes. This synchronizes resources and users between the OpenStack cloud provider and ManageIQ. By default, tenant mapping is disabled.
-
In the Default tab, under Endpoints, configure the host and authentication details of your OpenStack provider:
-
Select a Security Protocol method to specify how to authenticate the provider:
-
SSL without validation: Authenticate the provider insecurely using SSL.
-
SSL: Authenticate the provider securely using a trusted Certificate Authority. Select this option if the provider has a valid SSL certificate and it is signed by a trusted Certificate Authority. No further configuration is required for this option. This is the recommended authentication method.
-
Non-SSL: Connect to the provider insecurely using only HTTP protocol, without SSL.
-
-
In Hostname (or IPv4 or IPv6 address), enter the public IP or fully qualified domain name of the OpenStack Keystone service.
Note:
The hostname required here is also the OS_AUTH_URL value in the ~/overcloudrc file generated by the director (see Accessing the Overcloud in Red Hat OpenStack Platform Director Installation and Usage), or the ~/keystonerc_admin file generated by Packstack (see Evaluating OpenStack: Single-Node Deployment).
-
In API Port, set the public port used by the OpenStack Keystone service. By default, OpenStack uses port 5000 for non-SSL security protocol. For SSL, API port is 13000 by default.
-
In the Username field, enter the name of a user in the OpenStack environment.
In environments that use Keystone v3 authentication, the user must have the **admin** role for the relevant domain. -
In the Password field, enter the password for the user.
-
Click Validate to confirm ManageIQ can connect to the OpenStack provider.
-
-
Next, configure how ManageIQ should receive events from the OpenStack provider. Click the Events tab in the Endpoints section to start.
-
To use the Telemetry service of the OpenStack provider, select Ceilometer. Before you do so, the provider must first be configured accordingly. See Configuring the Overcloud to Store Events for details.
-
If you prefer to use the AMQP Messaging bus instead, or eventing is not enabled on Ceilometer, select AMQP and configure the following:
-
Select a Security Protocol method.
-
In Hostname (or IPv4 or IPv6 address) (of the Events tab, under Endpoints), enter the public IP or fully qualified domain name of the AMQP host.
-
In the API Port, set the public port used by AMQP. By default, OpenStack uses port 5672 for this.
-
In the Username field, enter the name of an OpenStack user with privileged access (for example, admin). Then, provide its corresponding password in the Password field.
-
Click Validate to confirm the credentials.
-
-
-
Click Add after configuring the cloud provider.
Note:
-
To collect inventory and metrics from an OpenStack environment, the ManageIQ appliance requires that the adminURL endpoint for the OpenStack environment be on a non-private network. Hence, the OpenStack adminURL endpoint should be assigned an IP address other than
192.168.x.x. Additionally, all the Keystone endpoints must be accessible, otherwise refresh will fail. -
Collecting capacity and utilization data from an OpenStack cloud provider requires selecting the Collect for All Clusters option under Configuration, in the settings menu. For information, see Capacity and Utilization Collections in the General Configuration Guide.
Configuring the Overcloud to Store Events
By default, the Telemetry service does not store events emitted by other services in a Red Hat OpenStack Platform environment. The following procedure outlines how to enable the Telemetry service on your OpenStack cloud provider to store such events. This ensures that events are exposed to ManageIQ when a Red Hat OpenStack Platform environment is added as a cloud provider.
-
Log in to the undercloud host.
-
Create an environment file called ceilometer.yaml, and add the following contents:
parameter_defaults: CeilometerStoreEvents: true -
Please see the below NOTE.
If your OpenStack cloud provider was not deployed through the undercloud, you can also set this manually. To do so:
-
Log in to your Controller node.
-
Edit /etc/ceilometer/ceilometer.conf, and specify the following option:
store_events = True
Note:
Passing the newly created environment file to the overcloud deployment is environment specific and requires executing commands in particular order depending on use of variables. For further information please see Director Installation and Usage in the Red Hat OpenStack Platform documentation.
Azure Providers
Adding Azure Providers
ManageIQ supports Microsoft Azure providers. Before ManageIQ can be authenticated to Microsoft Azure, you must complete a series of prerequisite steps using the Azure portal; see Create Active Directory application and service principal account using the Azure portal. Follow the steps to set up an Azure Active Directory (Azure AD) and assign the required permissions to it, then create an Azure Active Directory application, and obtain the Application ID (Client ID), Directory ID (Tenant ID), Subscription ID, and Key Value (Client Key) that are required to add and connect to the Azure instance as a provider in ManageIQ. Currently, all of these steps can be performed using either the Azure Resource Manager or Service Manager (Classic) mode.
Note:
In the steps described in Create Active Directory application and service principal account using the Azure portal:
-
The Application ID obtained during Get Application ID and Authentication Key is your Client ID. In the same section, after providing a description and a duration for the key, the VALUE displayed after clicking Save is your Client Key. If you choose an expiring key, make sure to note the expiration date, as you will need to generate a new key before that day in order to avoid an interruption.
-
The Directory ID obtained during Get Tenant ID is your Tenant ID. In Azure Active Directory (Azure AD), a tenant is a dedicated instance of the Azure AD service and is representative of an organization. It houses the users in a company and the information about them - their user profile data, permissions, groups, applications, and other information related to an organization and its security. To allow Azure AD users to sign in to your application, you must register your application in a tenant of your own which is assigned a Tenant ID (Directory ID).
-
During Assign Application to Role, select the Contributor role and not the Reader role.
-
To obtain your Subscription ID, log in to the Azure portal and click Subscriptions on the slide-out menu on the left. Find the appropriate subscription and see your Azure Subscription ID associated with it. Note that if the Subscriptions tab is not visible, then click on More services > to find it. The Azure Subscription ID is like a billing unit for all of the services consumed in your Azure account, including virtual machines and storage. The Subscription ID is in the form of a Globally Unique Identifier (GUID).
So, after a service principal account (instance of an application in a directory) has been created using the Azure portal, the following four pieces of information will be available within the Azure AD module.
-
Directory ID (Tenant ID)
-
Subscription ID
-
Application ID (Client ID)
-
Client Key
You can now use these values in the procedure below to add an Azure cloud instance as a provider to ManageIQ.
To Add an Azure Cloud Provider:
-
Browse to menu: Compute > Clouds > Providers.
-
Click Configuration, then click
 (Add a New Cloud Provider).
(Add a New Cloud Provider). -
Enter a Name for the provider.
-
From the Type list, select Azure.
-
Select a region from the Region list. One provider will be created for the selected region.
-
Enter Tenant ID.
-
Enter Subscription ID.
-
Enter Zone.
-
In the Credentials section, enter the Client ID and Client Key; click Validate.
-
Click Add.
Adding Azure Cloud Regions
ManageIQ allows administrators to add additional Azure cloud regions on the appliance server. You can use this capability to add new regions that have been set up since ManageIQ was released. Once added the region it will be available when creating a new Azure provider.
-
Click
 (Configuration).
(Configuration). -
Click on the Settings accordion, then click ManageIQ Region at the top.
-
Click on the Advanced tab.
-
Search for
:ems_azure:, and enter the regions you want to add under:additional_regions:.Example. To add hypothetical `lunar-base-1` `lunar-base-2` regions: :ems_azure: :additional_regions: :lunar-base-1: :name: lunar-base-1 :description: Lunar Base 1 :lunar-base-2: :name: lunar-base-2 :description: Lunar Base 2 -
Click Save.
Disabling Azure Cloud Regions
ManageIQ allows administrators to disable Azure cloud regions on the appliance server. You can use this capability to disable certain classified regions. Once disabled, the region will not be available when adding a new Azure provider.
-
Click
 (Configuration).
(Configuration). -
Click on the Settings accordion, then click Zones.
-
Click the zone where the ManageIQ server is located, then click on the EVM server.
-
Click on the Advanced tab.
-
Search for
:ems_azure:, and enter the regions you want to disable under:disabled_regions:.Example. To disable the `us-gov-arizona` and `us-gov-texas` regions: :ems_azure: :disabled_regions: - us-gov-arizona - us-gov-texas -
Click Save.
Amazon EC2 Providers
Permissions for Amazon EC2 Providers
Further limiting API access limitations can limit Automate capabilities, as Automate scripts directly access the AWS SDK to create brand new application functionality.
The AWS services primarily accessed by the ManageIQ API include:
-
Elastic Compute Cloud (EC2)
-
CloudFormation
-
CloudWatch
-
Elastic Load Balancing
-
Simple Notification Service (SNS)
-
Simple Queue Service (SQS)
Manually Creating an Amazon EC2 Role
To eliminate the need to assign Admin group privileges to the Amazon EC2 provider, create an IAM role following the procedure described in Creating a Role for an AWS Service (Console) in the Amazon Web Services documentation.
Use the following parameters:
-
Select EC2 as the service the role will use.
-
Attach the following permissions:
-
AmazonEC2FullAccess -
AmazonS3FullAccess -
AmazonSQSFullAccess
-
-
Enter
smartstatefor the Role name.
Once the IAM role is created, assign the provider Power User privileges as described in Permissions for Amazon EC2 Providers.
Adding Amazon EC2 Providers
Complete the following procedure to add an Amazon EC2 cloud provider in ManageIQ.
-
Browse to menu: Compute > Clouds > Providers.
-
Click Configuration, then click
 (Add a New Cloud Provider).
(Add a New Cloud Provider). -
Enter a Name for the provider.
-
From the Type list, select Amazon EC2.
-
Select a Region.
-
Select the appropriate Zone if you have more than one available.
-
Under Endpoints, click the Default tab.
-
Enter the Endpoint URL.
Note:
AWS allows users to set a custom endpoint URL when connecting to certain services, which you can add in the ManageIQ user interface per Amazon EC2 provider. See Interface VPC Endpoints (AWS PrivateLink) for more information.
-
Generate an Access Key in the Security Credentials of your Amazon AWS account. The Access Key ID acts as your User ID, and your Secret Access Key acts as your Password.
-
Click Validate to validate the credentials.
-
-
Click the SmartState Docker tab.
- Enter the SmartState Docker User Name and SmartState Docker Password.
-
Click Add.
Enabling Public AMIs from Amazon EC2
By default, public AMIs from an Amazon EC2 provider are not viewable in ManageIQ. To make these images viewable, you must edit the main configuration file for the appliance.
Note:
Syncing all public images may require additional memory resources. Also, bear in mind that syncing happens in each configured Amazon EC2 provider, which will require a similar amount of total memory resources.
-
Browse to the settings menu, then menu: Configuration > Zone > Advanced.
-
Select the configuration file to edit from the File list. If not already automatically selected, select EVM Server Main Configuration.
-
Set the get_public_images parameter:
-
Set the parameter to get_public_images: true to make public images viewable.
-
Set the parameter to get_public_images: false to make public images not viewable.
-
-
Optionally, configure an array of filters in public_images_filters to restrict which images are synced. See http://docs.aws.amazon.com/sdkforruby/api/Aws/EC2/Client.html#describe_images-instance_method for more details.
Enabling AWS Config Notifications
Amazon’s AWS Config notifies subscribers of changes in a region through its Simple Notification Service (SNS). ManageIQ subscribes to the SNS service for AWS Config deltas and converts the deltas into ManageIQ events.
-
Enable the AWS Config service in the AWS Management Console. See the AWS Config Developer Guide for more information.
-
Create a new Amazon SNS topic named
AWSConfig_topic. ManageIQ automatically connects to this topic. -
(Optional) Configure the frequency of delta creation in the AWS Management Console.
You can assign ManageIQ policies to the AWS events listed
below. The appliance performs a provider refresh on all these events
except for AWS_EC2_Instance_UPDATE.
| Event | Policies | Refresh |
|---|---|---|
AWS_EC2_Instance_CREATE |
src_vm vm_create |
ems |
AWS_EC2_Instance_UPDATE |
N/A |
ems |
AWS_EC2_Instance_running |
src_vm vm_start |
ems |
AWS_EC2_Instance_stopped |
src_vm vm_power_off |
ems |
AWS_EC2_Instance_shutting-down |
src_vm vm_power_off |
ems |
Enabling Amazon EC2 Events
After adding an Amazon EC2 provider and configuring an SNS topic in Enabling AWS Config Notifications, create a CloudTrail, then configure CloudWatch rules on your EC2 provider to automatically get events in ManageIQ for monitoring the provider.
Note:
The following procedures are accurate at time of publishing. See the Amazon AWS documentation for further details on these steps.
Creating a CloudTrail
In the CloudTrail area of the AWS Management Console, create a trail and an S3 bucket:
-
Create a Trail with a custom name.
-
(Optional) If you want to apply the trail to all of your ManageIQ regions, select Yes for Apply trail to all regions.
-
For Management Events, select Read/Write events: All.
-
Create a new S3 bucket.
Creating CloudWatch Rules Based on Event Patterns
In the CloudWatch area of the AWS Management Console, create three rules: one rule each for EC2, volumes, and snapshots.
To create a CloudWatch rule for EC2:
-
Browse to menu: Events > Rules and click Create rule.
-
Select the Event Pattern radio button to specify the event source.
-
Edit the Event Pattern Preview box, and paste and save the following code to create a rule based on a custom event pattern:
{ "source": [ "aws.ec2" ], "detail-type": [ "AWS API Call via CloudTrail" ], "detail": { "eventSource": [ "ec2.amazonaws.com" ] } } -
Click Add target and specify the following attributes:
-
Type:
SNS Topic -
Topic:
AWSConfig_topic -
Input:
Matched event
-
-
Click Configure Details to save these details.
-
Configure a name and description for the rule if desired. Ensure the Enabled checkbox is selected for State.
-
Click Create rule to save the CloudWatch rule.
Repeat the same procedure to create a CloudWatch rule for EC2 Instance State-changes:
-
Browse to menu: Events > Rules and click Create rule.
-
Select the Event Pattern radio button to specify the event source.
-
Edit the Event Pattern Preview box, and paste and save the following code to create a rule based on a custom event pattern:
{ "source": [ "aws.ec2" ], "detail-type": [ "EC2 Instance State-change Notification" ] } -
Click Add target and specify the following attributes:
-
Type:
SNS Topic -
Topic:
AWSConfig_topic -
Input:
Matched event
-
-
Click Configure Details to save these details.
-
Configure a name and description for the rule if desired. Ensure the Enabled checkbox is selected for State.
-
Click Create rule to save the CloudWatch rule.
Repeat the same procedure to create a CloudWatch rule for volumes, pasting the code snippet below to the Event Pattern Preview box:
-
Browse to menu: Events > Rules and click Create rule.
-
Select the Event Pattern radio button to specify the event source.
-
Edit the Event Pattern Preview box, and paste and save the following code to create a rule based on a custom event pattern:
{ "source": [ "aws.ec2" ], "detail-type": [ "EBS Volume Notification" ] } -
Click Add target and specify the following attributes:
-
Type:
SNS Topic -
Topic:
AWSConfig_topic -
Input:
Matched event
-
-
Click Configure Details to save these details.
-
Configure a name and description for the rule if desired. Ensure the Enabled checkbox is selected for State.
-
Click Create rule to save the CloudWatch rule.
Repeat the same procedure to create a CloudWatch rule for snapshots, pasting the code snippet below to the Event Pattern Preview box:
-
Browse to menu: Events > Rules and click Create rule.
-
Select the Event Pattern radio button to specify the event source.
-
Edit the Event Pattern Preview box, and paste and save the following code to create a rule based on a custom event pattern:
{ "source": [ "aws.ec2" ], "detail-type": [ "EBS Snapshot Notification" ] } -
Click Add target and specify the following attributes:
-
Type:
SNS Topic -
Topic:
AWSConfig_topic -
Input:
Matched event
-
-
Click Configure Details to save these details.
-
Configure a name and description for the rule if desired. Ensure the Enabled checkbox is selected for State.
-
Click Create rule to save the CloudWatch rule.
EC2 can now automatically refresh events in ManageIQ.
Adding Amazon Cloud Regions
ManageIQ allows administrators to add Amazon cloud regions on the appliance server. You can use this capability to add new regions that have been set up since ManageIQ was released. Once adding the region it will be available when creating a new Amazon EC2 provider.
-
Click
 (Configuration).
(Configuration). -
Click on the Settings accordion, then click ManageIQ Region at the top.
-
Click on the Advanced tab.
-
Search for
:ems_amazon:, and enter the regions you want to add under:additional_regions:.Example. To add hypothetical `lunar-base-1` `lunar-base-2` regions: :ems_amazon: :additional_regions: :lunar-base-1: :name: Lunar Base 1 :hostname: ec2.lunar-base-1.amazonaws.com :description: Lunar Base 1 :lunar-base-2: :name: Lunar Base 2 :hostname: ec2.lunar-base-2.amazonaws.com :description: Lunar Base 2 -
Click Save.
Disabling Amazon Cloud Regions
ManageIQ allows administrators to disable Amazon cloud regions on the appliance server. Use this capability to disable certain classified regions like AWS GovCloud. Once disabled, the region will not be available when adding an Amazon EC2 provider.
-
Click
 (Configuration).
(Configuration). -
Click on the Settings accordion, then click Zones.
-
Click the zone where the ManageIQ server is located, then click on the EVM server.
-
Click on the Advanced tab.
-
Search for
:ems_amazon:, and enter the regions you want to disable under:disabled_regions:.Example. To disable the `ap-northeast-1` region: :ems_amazon: :disabled_regions: - us-gov-west-1 - ap-northeast-1 -
Click Save.
Note:
In AWS, Government regions are disabled by default. To enable a disabled
region, be sure to do so in the production.yml configuration file
manually.
Refreshing Cloud Providers
Refresh a cloud provider to find other resources related to it. Ensure the chosen cloud providers have the correct credentials before refreshing.
-
Browse to menu: Compute > Clouds > Providers.
-
Select the checkboxes for the cloud providers to refresh.
-
Click Configuration, and then
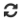 (Refresh Relationships and Power States).
(Refresh Relationships and Power States). -
Click OK.
Tagging Cloud Providers
Apply tags to all cloud providers to categorize them together at the same time.
-
Navigate to menu:Compute[Clouds > Providers].
-
Select the checkboxes for the Cloud Providers to tag.
-
Click
 (Policy), and then
(Policy), and then  (Edit Tags).
(Edit Tags). -
Select a customer tag to assign from the first list.

-
Select a value to assign from the second list.
-
Click Save.
Removing Cloud Providers
A cloud provider might require removal from the VMDB if it is no longer in use.
-
Browse to menu: Compute > Clouds > Providers.
-
Check the cloud providers to remove.
-
Click Configuration, and then
 (Remove Cloud Providers from the VMDB).
(Remove Cloud Providers from the VMDB). -
Click OK.
Editing a Cloud Provider
Edit information about a provider such as the name, IP address, and login credentials.
Note:
The Type value is unchangeable.
To use a different cloud provider, create a new one.
-
Browse to menu: Compute > Clouds > Providers.
-
Click the cloud provider to edit.
-
Click Configuration, and then
 (Edit
Selected Cloud Provider).
(Edit
Selected Cloud Provider). -
Edit the Basic Information. This varies depending on the Type of provider.
-
Fill out the Credentials by typing in a Username, Password, and a verification of this password (Confirm Password).
-
If selecting Amazon EC2, generate an Access Key in the Security Credentials of your Amazon AWS account. The Access Key ID acts as your User ID, and your Secret Access Key acts as your Password.
-
If selecting OpenStack, use the
Keystone User IDandPasswordfor your login credentials.
-
-
If editing an OpenStack provider, use the AMQP subtab to provide credentials required for the Advanced Message Queuing Protocol service on your OpenStack Nova component.
-
Click Validate and wait for notification of successful validation.
-
Click Save.
Viewing a Cloud Provider’s Timeline
View the timeline of events for instances registered to a cloud provider.
-
Navigate to menu:Compute[Clouds > Providers].
-
Click the desired cloud provider for viewing the timeline.
-
Click
 (Monitoring), and then
(Monitoring), and then
 (Timelines).
(Timelines). -
From Options, customize the period of time to display and the types of events to see.
-
Use Show to select regular Management Events or Policy Events.
-
Use the Type list to select hourly or daily data points.
-
Use Date to type the date for the timeline to display.
-
If you select to view a daily timeline, use Show to set how many days back to go. The maximum history is 31 days.
-
The three Event Groups list allow you to select different groups of events to display. Each has its own color.
-
From the Level list, select a Summary event, or a Detail list of events.
-
IBM Cloud VPC Provider
IBM Cloud Virtual Server for VPC
IBM Cloud Virtual Server for VPC (virtual private cloud) consists of virtual server instances within IBM’s VPC infrastructure, a public cloud construct. Virtual server instances for VPC enable the deployment of a secured private space in a publicly accessible environment by way of a single-tenant infrastructure in a multi-tenant public cloud. VPCs are logically isolated networks where cloud compute, storage and networking resources are deployed and used to host business workloads, applications and websites. Like networks in traditional on-premises data centers, VPCs utilize cloud security functions and models that match the functionality of those found in offline data centers.
Adding IBM Cloud VPC Providers
Complete the following procedure to add an IBM Cloud VPC provider in ManageIQ.
-
Browse to menu: Compute > Clouds > Providers.
-
Click Configuration, then click
 Add a New Cloud Provider.
Add a New Cloud Provider. -
From the Type list, select IBM Cloud VPC.
- Enter a Name for the provider.
- Select the appropriate Zone.
-
Select the appropriate Region.
-
Under Endpoint, enter your IBM Cloud API Key.
For more information on managing IBM Cloud API keys, including how to create one, see Managing user API keys.
-
Click Validate to validate the credentials.
Note: The connection uses port 443. Make sure the port 443 is opened on any firewalls.
- Click Add.
IBM Power Systems Virtual Servers Providers
IBM Power Systems Virtual Servers
IBM Power Systems Virtual Servers is a Power Systems infrastructure as a service (IaaS) offering with connectivity to the catalog of IBM Cloud Services that you can use to deploy a virtual server, also known as a logical partition (LPAR), in a matter of minutes. IBM Power Systems clients who have typically relied upon on-premises-only infrastructure can now quickly and economically extend their Power IT resources off-premises.
Adding IBM Power Systems Virtual Servers Providers
Complete the following procedure to add an IBM Power Systems Virtual Servers cloud provider in ManageIQ.
-
Browse to menu: Compute > Clouds > Providers.
-
Click Configuration, then click
 (Add a New Cloud Provider).
(Add a New Cloud Provider). -
From the Type list, select IBM Power Systems Virtual Servers.
-
Enter a Name for the provider.
-
Select the appropriate Zone.
-
Under Endpoints, in the Default tab.
-
Enter your IBM Cloud API Key.
For more information on managing IBM Cloud API keys, including how to create one, refer to IBM Cloud Docs: Managing user API keys
-
Enter the PowerVS Service GUID of the IBM Power Systems Virtual Servers service instance you want to add.
You can easily copy the GUID from the IBM Cloud Resources page, by selecting “Services” and clicking on the whitespace of a PowerVS instance row.
-
Click Validate to validate the credentials.
-
-
Click Add.
IBM PowerVC Providers
IBM PowerVC
IBM PowerVC is an advanced virtualization and cloud management offering. Built on OpenStack, it provides simplified virtualization management and cloud deployments for IBM AIX®, IBM i and Linux virtual machines (VMs) running on IBM Power Systems™. The offering is designed to build private cloud capabilities on Power Systems servers and improve administrator productivity. It can further integrate with cloud environments through higher-level cloud orchestrators.
Adding IBM PowerVC Providers
Complete the following procedure to add an IBM PowerVC cloud provider in ManageIQ.
-
Browse to menu: Compute > Clouds > Providers.
-
Click Configuration, then click
 (Add a New Cloud Provider).
(Add a New Cloud Provider). -
From the Type list, select IBM PowerVC.
-
Enter a Name for the provider.
-
Select the appropriate Zone.
-
Enter the PowerVC region in Provider Region.
-
Select the appropriate Domain ID.
-
(Optional) Enable tenant mapping by toggling the Tenant Mapping Enabled option to On. This synchronizes resources and users between the IBM PowerVC provider and ManageIQ. By default, tenant mapping is disabled.
-
Under Endpoints, in the Default tab:
-
Select a Security Protocol method to specify how to authenticate the provider:
-
SSL without validation: Authenticate the provider insecurely using SSL.
-
SSL: Authenticate the provider securely using a trusted Certificate Authority. Select this option if the provider has a valid SSL certificate and it is signed by a trusted Certificate Authority. No further configuration is required for this option. This is the recommended authentication method.
-
Non-SSL: Connect to the provider insecurely using only HTTP protocol, without SSL.
-
-
In PowerVC API Endpoint (Hostname or IPv4/IPv6 address), enter the public IP or fully qualified domain name of the PowerVC API endpoint.
-
In API Port, set the public port used by the PowerVC API. By default, PowerVC is configured to use port 5000.
-
In the API Username field, enter the name of a user in the PowerVC environment.
The user must have the **admin** role for the relevant domain. -
In the API Password field, enter the password for the user.
-
Click Validate to confirm ManageIQ can connect to the PowerVC provider.
-
-
Click Add.
Network Managers
In ManageIQ, a network manager is an inventory of networking entities on existing cloud and infrastructure providers managed by your ManageIQ appliance.
This provider type exposes software-defined networking (SDN) providers including OpenStack Network (Neutron), Azure Network, and Amazon EC2 Network, which enables software-defined networking inventory collection. The OpenStack Network provider collects inventory of floating IPs from OpenStack so that IPs can be allocated without querying OpenStack database every time. Also, it refreshes all Neutron data from both OpenStack and OpenStack Infrastructure, and extracts the Neutron logic to a shared place. Note that management via the network providers configuration is currently disabled.
This chapter describes the different types of network managers available to ManageIQ, and how to manage them. Network managers are discovered automatically by ManageIQ from other connected providers.
Adding or Viewing Network Providers
Note:
All supported network providers — OpenStack Network, Azure Network, and Amazon EC2 Network, are added or removed automatically upon adding or removing the respective cloud provider.
Viewing network providers:
-
Browse to menu: Networks > Providers to see a list of all network providers, along with information such as Name, Type, EVM Zone, Number of Instances, Subnets, and Region.
-
Click on a provider from the list to view its summary screen.
Network providers summary:
The summary screen includes tables containing information on Properties, Status, Relationships, Overview, and Smart Management. Click on rows in the Relationship and Overview tables to see detailed information for individual entities.
Accordion tabs in the sidebar provide access to Properties and Relationships details.
Click on Reload, Configuration, Policy, and Monitoring actions in the taskbar to manage the selected provider.
Note:
Alternatively, click on a cloud provider to see the cloud provider details and its relationships such as Network Manager, Tenants, Instances among others. In Relationships, click Network Manager to see information about the network provider, and its relationship with the cloud provider, on the summary page.
Refreshing Network Providers
Refresh a network provider to find other resources related to it. Ensure the selected network providers have the correct credentials before refreshing.
-
Browse to menu: Networks > Providers.
-
Select the network providers to refresh.
-
Click Configuration, and then
 (Refresh Relationships and Power States).
(Refresh Relationships and Power States). -
Click OK.
Tagging Network Providers
Apply tags to network providers to categorize them together at the same time.
-
Navigate to menu:Networks[Providers].
-
Select the network providers to tag.
-
Click
 (Policy), and then
(Policy), and then  (Edit Tags).
(Edit Tags). -
Select a customer tag to assign from the first list.
-
Select a value to assign from the second list.
-
Click Save.
Removing Network Providers
Although network providers are added or removed automatically upon adding or removing the respective cloud provider, you can manually remove a network provider if it is no longer in use. This will remove the network provider from the VMDB and any relationship with the cloud provider.
-
Browse to menu: Networks > Providers.
-
Click the network provider to remove.
-
Click Configuration, and then
 (Remove this Network Provider from the VMDB).
(Remove this Network Provider from the VMDB). -
Click OK.
Viewing a Network Provider’s Timeline
View the timeline of events for instances registered to a network provider.
-
Navigate to menu:Networks[Providers].
-
Click the network provider you want to monitor the timeline for.
-
Click
 (Monitoring), and then
(Monitoring), and then
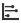 (Timelines).
(Timelines). -
From Options, select the event type and interval, and customize the period of time to display and the types of events to see.
-
Select Management Events or Policy Events from the Show list.
-
Select an Interval between Hourly and Daily.
-
Select Date.
-
If you selected Daily for Interval, set the number of days in the past to see the event timeline for. The maximum is 31 days back.
-
Select Summary or Detail for Level.
-
Select the required Event Groups from the lists you want to monitor the timeline for.
-
You can also assign policy profiles to network providers, or remove them. The method for doing so is similar to that of any normal policy profile.
Using the Topology Widget for Network Providers
The Topology widget is an interactive topology graph, showing the status and relationships between the different entities of the network providers that ManageIQ has access to.
The topology graph includes cloud subnets, virtual machines, security groups, floating IP addresses, cloud networks, network routers, cloud tenants, and tags within the overall network provider environment.
Each entity in the graph displays a color indication of its status: green indicates an active entity, while red indicates inactivity or an issue.
-
Browse to menu: Networks > Topology.
-
Click the desired network provider for viewing the provider summary.
Alternatively, you can open the topology widget from the provider summary page by clicking Topology under Overview.
-
Hovering over any individual graph element will display a summary of details for the individual element.
-
Double-click an entity in the graph to browse to its summary page.
-
Drag elements to reposition the graph.
-
Click the symbols in the legend at the top of the graph to show or hide entities.
-
Click the Display Names checkbox to show or hide entity names.
-
Click Refresh to refresh the display of the network provider entities.
-
Enter a search term in the Search box to locate an entity by full or partial name.
Containers Providers
A containers provider is a service that manages container resources, that can be added to the ManageIQ appliance.
ManageIQ can connect to OpenShift Container Platform containers providers and manage them similarly to infrastructure and cloud providers. This allows you to gain control over different aspects of your containers environment and answer questions such as:
-
How many containers exist in my environment?
-
Does a specific node have enough resources?
-
How many distinct images are used?
-
Which image registries are used?
When ManageIQ connects to a container’s environment, it collects information on different areas of the environment:
-
Entities such as pods, nodes, or services.
-
Basic relationships between the entities, for example: Which services are serving which pods?
-
Advanced insight into relationships, for example: Which two different containers are using the same image?
-
Additional information, such as events, projects, routes, and metrics.
You can manage policies for containers entities by adding tags. All containers entities except volumes can be tagged.
Note:
This chapter provides details on managing containers providers. For details on working with the resources within a container environment, see Container Entities in Managing Infrastructure and Inventory.
The ManageIQ user interface uses virtual thumbnails to represent containers providers. Each thumbnail contains four quadrants by default, which display basic information about each provider:
![]()
-
Number of nodes
-
Container provider software
-
Power state
-
Authentication status
| Icon | Description |
|---|---|
 |
Validated: Valid authentication credentials have been added. |
 |
Invalid: Authentication credentials are invalid. |
 |
Unknown: Authentication status is unknown or no credentials have been entered. |
Containers provider authentication status
Obtaining an OpenShift Container Platform Management Token
When deploying OpenShift using openshift-ansible-3.0.20 (or later
versions), the OpenShift Container Platform service account
and roles required by ManageIQ are installed by default.
For newer versions of OpenShift you have to create a service-account with the proper permissions for ManageIQ.
- Create a namespace for the service account
project_name="management-manageiq" # Pick a name for your project oc adm new-project $project_name --description="ManageIQ Project" - Create a service account in that project
service_account_name="management-admin" oc create serviceaccount $service_account_name -n $project_name - Create the cluster role
echo '{"apiVersion": "v1", "kind": "ClusterRole", "metadata": {"name": "management-manageiq-admin"}, "rules": [{"resources": ["pods/proxy"], "verbs": ["*"]}]}' | oc create -f - - Apply roles and policies to the service account
oc policy add-role-to-user -n $project_name admin -z $service_account_name oc policy add-role-to-user -n $project_name management-manageiq-admin -z $service_account_name oc adm policy add-cluster-role-to-user cluster-reader system:serviceaccount:$project_name:$service_account_name oc adm policy add-scc-to-user privileged system:serviceaccount:$project_name:$service_account_name oc adm policy add-cluster-role-to-user self-provisioner system:serviceaccount:$project_name:$service_account_name
Note:
See the OpenShift Container Platform documentation for a list of the default roles.
Run the following to obtain the token needed to add an OpenShift Container Platform provider:
# oc sa get-token -n $project_name $service_account_name
eyJhbGciOiJSUzI1NiI...
Enabling OpenShift Cluster Metrics
Use the OpenShift Cluster Metrics plug-in to collect node, pod, and container metrics into one location. This helps track usage and find common issues.
-
Configure ManageIQ to allow for all three Capacity & Utilization server roles.
-
Enable cluster metrics using the OpenShift Container Platform documentation.
Adding an OpenShift Container Platform Provider
After initial installation and creation of a ManageIQ environment, add an OpenShift Container Platform provider using the token obtained in Obtaining an OpenShift Container Platform Management Token and following the procedure below.
-
Browse to menu: Compute > Containers > Providers.
-
Click Configuration, then click
 (Add a New Containers Provider).
(Add a New Containers Provider). -
Enter a Name for the provider.
-
From the Type list, select OpenShift Container Platform.
-
Enter the appropriate Zone for the provider. If you do not specify a zone, it is set to
default. -
In the Default tab, configure the following for the OpenShift provider:
-
Select a Security Protocol method to specify how to authenticate the provider:
-
SSL: Authenticate the provider securely using a trusted Certificate Authority. Select this option if the provider has a valid SSL certificate and it is signed by a trusted Certificate Authority. No further configuration is required for this option.
-
SSL trusting custom CA: Authenticate the provider with a self-signed certificate. For this option, copy your provider’s CA certificate to the Trusted CA Certificates box in PEM format.
Note:
You can obtain your OpenShift Container Platform provider’s CA certificate for all endpoints (default, metrics, alerts) from
/etc/origin/master/ca.crt. Paste the output (a block of text starting with-----BEGIN CERTIFICATE-----) into the Trusted CA Certificates field. -
SSL without validation: Authenticate the provider insecurely (not recommended).
-
-
Enter the Hostname (or IPv4 or IPv6 address) of the provider.
Important:
The Hostname must use a unique fully qualified domain name.
-
Enter the API Port of the provider. The default port is
8443. -
Enter a token for your provider in the Token box.
Note:
To obtain a token for your provider, run the
oc get secretcommand on your provider; see Obtaining an OpenShift Container Platform Management Token.For example:
# oc get secret –namespace management-infra management-admin-token-8ixxs –template=’’ | base64 –decode
-
Click Validate to confirm that ManageIQ can connect to the OpenShift Container Platform provider.
-
-
In the Alerts endpoint tab optionally configure the alerts service:
-
Select a service type, or leave disabled. Prometheus alerts are only supported on OCP v3
-
Select a Security Protocol method to specify how to authenticate the service:
-
SSL: Authenticate the provider securely using a trusted Certificate Authority. Select this option if the provider has a valid SSL certificate and it is signed by a trusted Certificate Authority. No further configuration is required for this option.
-
SSL trusting custom CA: Authenticate the provider with a self-signed certificate. For this option, copy your provider’s CA certificate to the Trusted CA Certificates box in PEM format.
-
SSL without validation: Authenticate the provider insecurely using SSL. (Not recommended)
-
-
Enter the Hostname (or IPv4 or IPv6 address) or alert Route.
-
Enter the API Port if your Prometheus provider uses a non-standard port for access. The default port is
443. -
Click Validate to confirm that ManageIQ can connect to the alerts service.
-
-
In the Metrics endpoint tab optionally configure the metrics service details:
-
Select a service type (Prometheus or Hawkular) or leave disabled
-
Select a Security Protocol method to specify how to authenticate the service:
-
SSL: Authenticate the provider securely using a trusted Certificate Authority. Select this option if the provider has a valid SSL certificate and it is signed by a trusted Certificate Authority. No further configuration is required for this option.
-
SSL trusting custom CA: Authenticate the provider with a self-signed certificate. For this option, copy your provider’s CA certificate to the Trusted CA Certificates box in PEM format.
Note:
In OpenShift, the default deployment of the router generates certificates during installation, which can be used with the SSL trusting custom CA option. Connecting a Hawkular endpoint with this option requires the CA certificate that the cluster uses for service certificates, which is stored in
/etc/origin/master/service-signer.crton the first master in a cluster. -
SSL without validation: Authenticate the provider insecurely using SSL. (Not recommended)
-
-
Enter the Hostname (or IPv4 or IPv6 address) of the metrics service.
In order to find the hostname you can use the
oc get routecommand.On OCPv4 you can get the Prometheus route by running:
oc get route prometheus-k8s -n openshift-monitoringExample:
oc get route prometheus-k8s -n openshift-monitoring NAME HOST/PORT PATH SERVICES PORT TERMINATION WILDCARD prometheus-k8s prometheus-k8s-openshift-monitoring.ocp.example.com prometheus-k8s web reencrypt/Redirect NoneIn this example you would use
prometheus-k8s-openshift-monitoring.ocp.example.comas the metrics hostname.On OCPv3 you can get the Hawkular route by running:
oc get route hawkular-metrics -n openshift-infraOr the Prometheus route:
oc get route prometheus -n openshift-metrics -
Enter the API Port if your Hawkular or Prometheus provider uses a non-standard port for access. The default port is
443. -
Click Validate to confirm that ManageIQ can connect to the metrics endpoint.
-
-
Click the Advanced tab to add image inspector settings for scanning container images on your provider using OpenSCAP.
Note:
-
These settings control downloading the image inspector container image from the registry and obtaining the Common Vulnerabilities and Exposures (CVE) information (for effective scanning) via a proxy.
-
CVE URL that ManageIQ requires to be open for OpenSCAP scanning: https://www.redhat.com/security/data/metrics/ds/. This information is based on the source code of OpenSCAP.
-
Enter the proxy information for the provider in either HTTP, HTTPS, or NO Proxy depending on your environment.
-
Enter the Image-Inspector Repository information. For example,
openshift3/image-inspector. -
Enter the Image-Inspector Registry information. For example,
registry.access.redhat.com. -
Enter the Image-Inspector Tag value. A tag is a mark used to differentiate images in a repository, typically by the application version stored in the image.
-
Enter
https://www.redhat.com/security/data/metrics/ds/in CVE location.
-
-
Click Add.
Note:
You can also set global default image-inspector settings for all
OpenShift providers in the advanced settings menu by editing the values
under ems_kubernetes, instead of setting this for each provider.
For example:
:image_inspector_registry: registry.access.redhat.com
:image_inspector_repository: openshift3/image-inspector
Adding an Azure Kubernetes Service (AKS) Container Provider
After initial installation and creation of a ManageIQ environment you can add an Azure Kubernetes Service Container provider.
You will need to retrieve the cluster hostname and the cluster_admin token.
Navigate to your AKS cluster in the Azure Portal (https://portal.azure.com). In the Overview tab search for the API server address. This is the hostname that you will need when you create your provider.
Next you need to retrieve your cluster_admin token, click on the Connect button. This will open a panel with instructions on running the az command line utility in Azure Cloud Shell (you can also run this locally if you have the az utility installed).
az account set --subscription SUBSCRIPTION_ID
az aks get-credentials --admin --resource-group RESOURCE_GROUP_NAME --name CLUSTER_NAME
Merged "CLUSTER_NAME-admin" as current context in ~/.kube/config
Now grab the token for your user out of the ~.kube/config file. If this is the only cluster configured in your ~/.kube/config then you can simply run:
grep 'token: ' .kube/config
token: abcdefghijklmnopqrstuvwxyzabcdefghijklmnopqrstuvwxyzabcdefghijklmnopqrstuvwxyzabcdefghijklmnopqrstuvwxyzabcdefghijklmnopqrstuvwx
If you already have multiple clusters configured search for your AKS cluster admin user, it will be named clusterAdmin_${RESOURCE_GROUP_NAME}_${CLUSTER_NAME}
-
Browse to menu: Compute > Containers > Providers.
-
Click Configuration, then click
 (Add a New Containers Provider).
(Add a New Containers Provider). -
Enter a Name for the provider.
-
From the Type list, select Azure Kubernetes Service.
-
Enter the appropriate Zone for the provider. If you do not specify a zone, it is set to
default. -
In the Default tab, configure the following for the AKS provider:
-
Select a Security Protocol method to specify how to authenticate the provider:
-
SSL: Authenticate the provider securely using a trusted Certificate Authority. Select this option if the provider has a valid SSL certificate and it is signed by a trusted Certificate Authority. No further configuration is required for this option.
-
SSL trusting custom CA: Authenticate the provider with a self-signed certificate. For this option, copy your provider’s CA certificate to the Trusted CA Certificates box in PEM format.
-
SSL without validation: Authenticate the provider insecurely (not recommended).
-
-
Enter the Hostname of the provider that you obtained earlier.
Important:
The Hostname must use a unique fully qualified domain name.
-
Enter the API Port of the provider. The default port is
443. -
Enter the token that you obtained earlier for your provider in the Token box.
-
Click Validate to confirm that ManageIQ can connect to the Azure Kubernetes Service provider.
-
-
Click Add.
Adding an Oracle Kubernetes Engine (OKE) Container Provider
After initial installation and creation of a ManageIQ environment you can add an Oracle Kubernetes Engine Container provider.
-
Browse to menu: Compute > Containers > Providers.
-
Click Configuration, then click
 (Add a New Containers Provider).
(Add a New Containers Provider). -
From the Type list, select Oracle Kubernetes Engine.
-
Enter a Name for the provider.
-
Enter the appropriate Zone for the provider. If you do not specify a zone, it is set to
default. -
Select the provider region where your Oracle Kubernetes Cluster is located
-
Next you will need to gather your Oracle Tenant ID from https://cloud.oracle.com/tenancy, and use the
Copylink to fetch your tenant OCID. -
Now you need to enter the Cluster ID of your OKE cluster. This can be found on the
Cluster Detailstab on your cluster’s dashboard atCluster Id. Use theCopylink to copy this ID. -
In the Default tab, configure the following for the OKE provider:
-
Select a Security Protocol method to specify how to authenticate the provider:
-
SSL: Authenticate the provider securely using a trusted Certificate Authority. Select this option if the provider has a valid SSL certificate and it is signed by a trusted Certificate Authority. No further configuration is required for this option.
-
SSL trusting custom CA: Authenticate the provider with a self-signed certificate. For this option, copy your provider’s CA certificate to the Trusted CA Certificates box in PEM format.
-
SSL without validation: Authenticate the provider insecurely (not recommended).
-
-
Enter the Hostname of the cluster, you can obtain this from the
Cluster Detailspage atKubernetes API Public Endpoint -
Enter the API Port of the cluster. The default port is
6443. -
Enter the Oracle User ID for the user that you want ManageIQ to use to access your account. You can get this from the
Profiledropdown and clicking on your username. Then use theCopylink to copy the OCID for your user. -
Next copy and paste the public key for your user’s Auth Token. If you do not have one yet you can create an Auth Token by going to your user profile and selecting
Auth TokensunderResourcesand select theGenerate Tokenbutton. -
Now copy and paste your private key from the same auth token.
-
Click Validate to confirm that ManageIQ can connect to the Oracle Kubernetes Engine provider.
-
-
Click Add.
Tagging Containers Providers
Apply tags to all containers providers to categorize them together at the same time.
-
Navigate to menu:Compute[Containers > Providers].
-
Select the checkboxes for the containers providers to tag.
-
Click
 (Policy), and then
(Policy), and then  (Edit Tags).
(Edit Tags). -
Select a tag to assign from the drop-down menu.

-
Select a value to assign.
-
Click Save.
Removing Containers Providers
You may want to remove a containers provider from the VMDB if the provider is no longer in use.
-
Browse to menu: Compute > Containers > Providers.
-
Select the checkboxes for the containers providers to remove.
-
Click Configuration, and then
 (Remove Containers Providers from Inventory).
(Remove Containers Providers from Inventory). -
Click OK.
Editing a Containers Provider
Edit information about a provider such as the name, hostname, IP address or port, and credentials as required. If you have just upgraded your ManageIQ environment from an older version, edit the provider to specify the authentication method the provider uses to connect to ManageIQ.
-
Browse to menu: Compute > Containers > Providers.
-
Click the containers provider to edit.
-
Click Configuration, and then
 (Edit Selected Containers Provider).
(Edit Selected Containers Provider). -
Edit the Name if required.
Note:
The Type value is unchangeable.
-
Under Endpoints in the Default tab, edit the following as required:
-
Select a Security Protocol method to specify how to authenticate the provider:
-
SSL: Authenticate the provider securely using a trusted Certificate Authority. Select this option if the provider has a valid SSL certificate and it is signed by a trusted Certificate Authority. No further configuration is required for this option.
-
SSL trusting custom CA: Authenticate the provider with a self-signed certificate. For this option, copy your provider’s CA certificate to the Trusted CA Certificates box in PEM format.
Note:
You can obtain your OpenShift Container Platform provider’s CA certificate for all endpoints (default, metrics, alerts) from
/etc/origin/master/ca.crt. Paste the output (a block of text starting with-----BEGIN CERTIFICATE-----) into the Trusted CA Certificates field. -
SSL without validation: Authenticate the provider insecurely (not recommended).
-
-
Enter the Hostname (or IPv4 or IPv6 address) of the provider.
Important:
The Hostname must use a unique fully qualified domain name.
-
Enter the API Port of the provider. The default port is
8443. -
Enter a token for your provider in the Token box.
Note:
To obtain a token for your provider, run the
oc get secretcommand on your provider; see Obtaining an OpenShift Container Platform Management Token.For example:
# oc get secret –namespace management-infra management-admin-token-8ixxs –template=’’ | base64 –decode
-
Click Validate to confirm that ManageIQ can connect to the OpenShift Container Platform provider.
-
-
Under Endpoints in the Metrics tab, configure the following for gathering capacity and utilization metrics for Hawkular or Prometheus based on the selection:
-
Select a Security Protocol method to specify how to authenticate the provider:
-
SSL: Authenticate the provider securely using a trusted Certificate Authority. Select this option if the provider has a valid SSL certificate and it is signed by a trusted Certificate Authority. No further configuration is required for this option.
-
SSL trusting custom CA: Authenticate the provider with a self-signed certificate. For this option, copy your provider’s CA certificate to the Trusted CA Certificates box in PEM format.
-
SSL without validation: Authenticate the provider insecurely using SSL. (Not recommended)
-
-
Enter the Hostname (or IPv4 or IPv6 address) of the provider.
-
Enter the API Port if your provider uses a non-standard port for access. The default port is
443. -
Click Validate to confirm that ManageIQ can connect to the endpoint.
-
-
Under Endpoints in the Alerts tab, configure the following for Prometheus alerting from the cluster.
-
SSL: Authenticate the provider securely using a trusted Certificate Authority. Select this option if the provider has a valid SSL certificate and it is signed by a trusted Certificate Authority. No further configuration is required for this option.
-
SSL trusting custom CA: Authenticate the provider with a self-signed certificate. For this option, copy your provider’s CA certificate to the Trusted CA Certificates box in PEM format.
-
SSL without validation: Authenticate the provider insecurely using SSL. (Not recommended)
-
Enter the Hostname (or IPv4 or IPv6 address) of the provider.
-
Enter the API Port if your provider uses a non-standard port for access. The default port is
443. -
Click Validate to confirm that ManageIQ can connect to the endpoint.
-
-
-
Click Save.
Hiding Environment Variables for Containers Providers
You can restrict users from viewing container provider environment variables by configuring user roles.
This is useful as the environment variables panel can expose sensitive information, such as passwords, that you may not want certain users to view.
Note:
The default user roles in ManageIQ are read-only. To customize a role’s settings, create a new role or a copy of an existing role.
You can view role information and the product features the role can access (marked by a checkmark) by clicking on any role in Access Control. Expand the categories under Product Features to see further detail.
To configure user access to container environment variables:
-
Click
 (Configuration).
(Configuration). -
Click the Access Control accordion, then click Roles.
-
Select a existing custom role from the Access Control Roles list, and click
 (Configuration), then
(Configuration), then  (Edit the selected Role).
(Edit the selected Role).Alternatively, to create a new custom role, select a role from the Access Control Roles list, and click
 (Configuration), then
(Configuration), then  (Copy this Role to a new Role).
(Copy this Role to a new Role). -
Edit the name for the role if desired.
-
For Access Restriction for Services, VMs, and Templates, select if you want to limit users with this role to only see resources owned by the user or their group, owned by the user, or all resources (None).
-
Expand the Product Features (Editing) tree options to show menu:Everything[Compute > Containers > Containers Explorer > All Containers > View Containers].
-
Clear the Environment Variables checkbox to restrict the user role from viewing container environment variables.
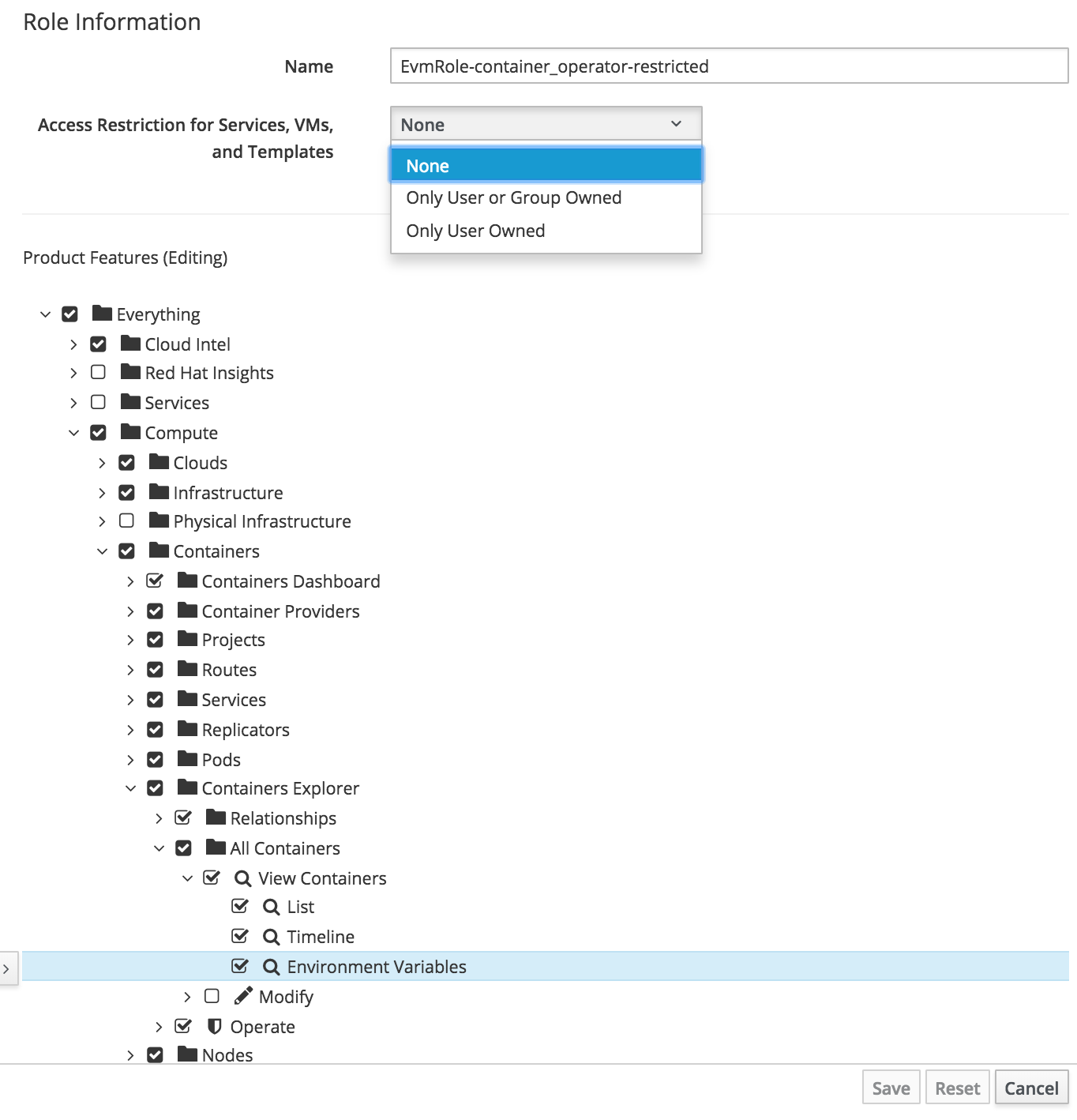
-
Click Save.
For more information about user roles, see Roles in General Configuration.
Viewing a Containers Provider’s Timeline
View the timeline of events for instances registered to a containers provider.
-
Navigate to menu:Compute[Containers > Providers].
-
Click the desired containers provider for viewing the timeline.
-
Click
 (Monitoring), and then
(Monitoring), and then
 (Timelines).
(Timelines). -
From Options, customize the period of time to display and the types of events to see.
-
Use Show to select regular Management Events or Policy Events.
-
Use the Interval dropdown to select hourly or daily data points.
-
Use Date to type the date for the timeline to display.
-
If you select to view a daily timeline, use Show to set how many days back to go. The maximum history is 31 days.
-
From the Level dropdown, select a Summary event, or a Detail list of events.
-
The three Event Groups dropdowns allow you to select different groups of events to display. Each has its own color.
-
Click on an item for more detailed information.
Storage Managers
In ManageIQ, a storage manager is a service providing storage resources that you can manage from a ManageIQ appliance. This chapter describes the different types of storage managers used by ManageIQ, and how they are added to ManageIQ.
There are three types of storage managers currently available to ManageIQ:
-
Amazon Elastic Block Store
-
OpenStack Block Storage (
openstack-cinder) -
OpenStack Object Storage (
openstack-swift)
Amazon Elastic Block Store Managers
The Amazon Elastic Block Store service provides and manages persistent block storage resources that Amazon EC2 instances can consume.
To use the Amazon Elastic Block Store service as a storage manager, you must first add an Amazon EC2 cloud provider to your ManageIQ appliance. The Amazon Elastic Block Store service is automatically discovered by ManageIQ, and added to the Storage Managers list. See Adding Amazon EC2 Providers for instructions on adding an Amazon EC2 cloud provider.
OpenStack Block Storage Managers
The OpenStack Block Storage service (openstack-cinder) provides and
manages persistent block storage resources that OpenStack infrastructure
instances can consume.
To use OpenStack Block Storage as a storage manager, you must first add an OpenStack cloud provider to your ManageIQ appliance and enable events. The Block Storage service will be automatically discovered by ManageIQ and added to the Storage Managers list in ManageIQ. See Adding OpenStack Providers for instructions on adding a cloud provider and enabling events.
OpenStack Block Storage Manager Targeted Refresh
ManageIQ supports targeted refresh of OpenStack Block Storage
(Cinder) volumes. This functionality automatically pulls down new
inventory data for an object when ManageIQ receives an
event from the OpenStack provider. For example, if
ManageIQ receives a volume.update.end event from Cinder,
instead of refreshing the entire inventory, it performs a targeted
refresh of the volume referenced in the event.
OpenStack Object Storage Managers
The OpenStack Object Storage (openstack-swift) service provides cloud
object storage.
To use the OpenStack Object Storage service as a storage manager, you must first add an OpenStack cloud provider to your ManageIQ appliance and enable events. The Object Storage service will be automatically discovered by ManageIQ and added to the Storage Managers list in ManageIQ. See Adding OpenStack Providers for instructions on adding a cloud provider and enabling events.
Viewing Object Stores
The object store summary page shows details including the object store’s size, parent cloud, storage manager, cloud tenant, and the number of cloud objects on the object store.
In ManageIQ, view object stores on a object storage manager by following these steps:
-
Browse to menu: Storage > Object Stores to display a list of object store containers.
-
Click a container to open a summary page for that object store container.
-
Click Cloud Objects to view a list of object stores in the object store container.
-
Click an object store from the list to view the object store’s summary page.
Appendix
Using a Self-Signed CA Certificate
Adding a self-signed Certificate Authority (CA) certificate for SSL authentication requires more configuration on OpenStack Platform and Microsoft System Center Virtual Machine Manager (SCVMM) providers.
Note: This procedure is not required for OpenShift Container Platform, Red Hat Virtualization, or middleware manager providers, which have the option to select SSL trusting custom CA as a Security Protocol in the user interface. These steps are needed only for providers without this option in the user interface.
Before adding the provider, configure the following:
-
Copy your provider’s CA certificate in PEM format to
/etc/pki/ca-trust/source/anchors/on your ManageIQ appliance. -
Update the trust settings on the appliance:
# update-ca-trust -
Restart the EVM processes on the server:
# rake evm:restart
The CA certificate is added to the appliance, and you can add the provider to ManageIQ.
